Join our community to see how developers are using Workik AI everyday.
Features

Automate HTTP Headers
AI generates Content-Security-Policy and X-Frame-Options headers, configuring them for Node.js, Django, and more servers.

Integrate with CI/CD
Automate header deployment in GitHub Actions or Jenkins pipelines, for consistent security across environments.

Validate Headers Instantly
Use AI to test Strict-Transport-Security and CSP headers with OWASP ZAP or browser DevTools.

Customize Advanced Policies
AI configures Access-Control-Allow-Origin and dynamic CSPs for APIs tailored to React, Vue.js, or more.
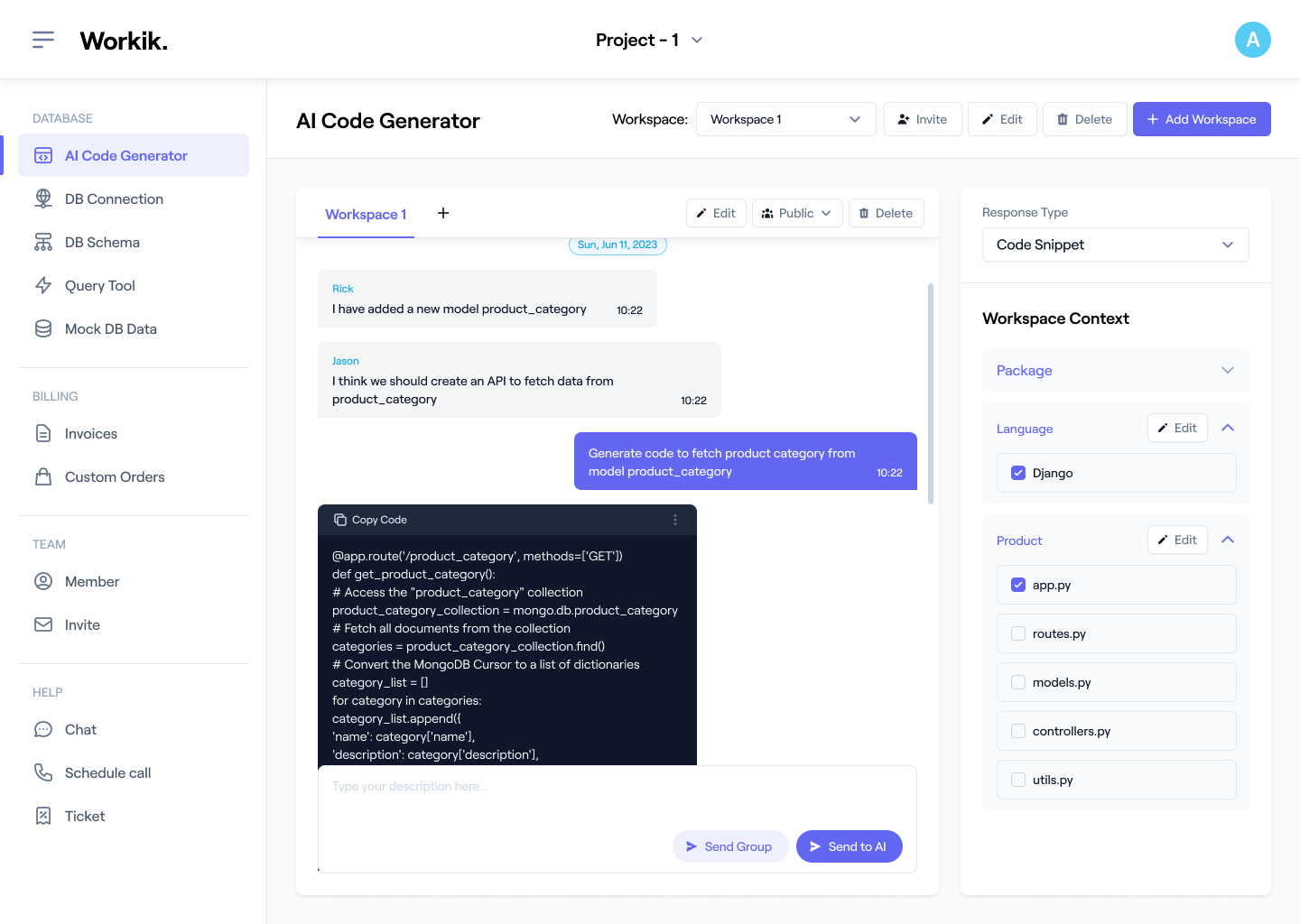
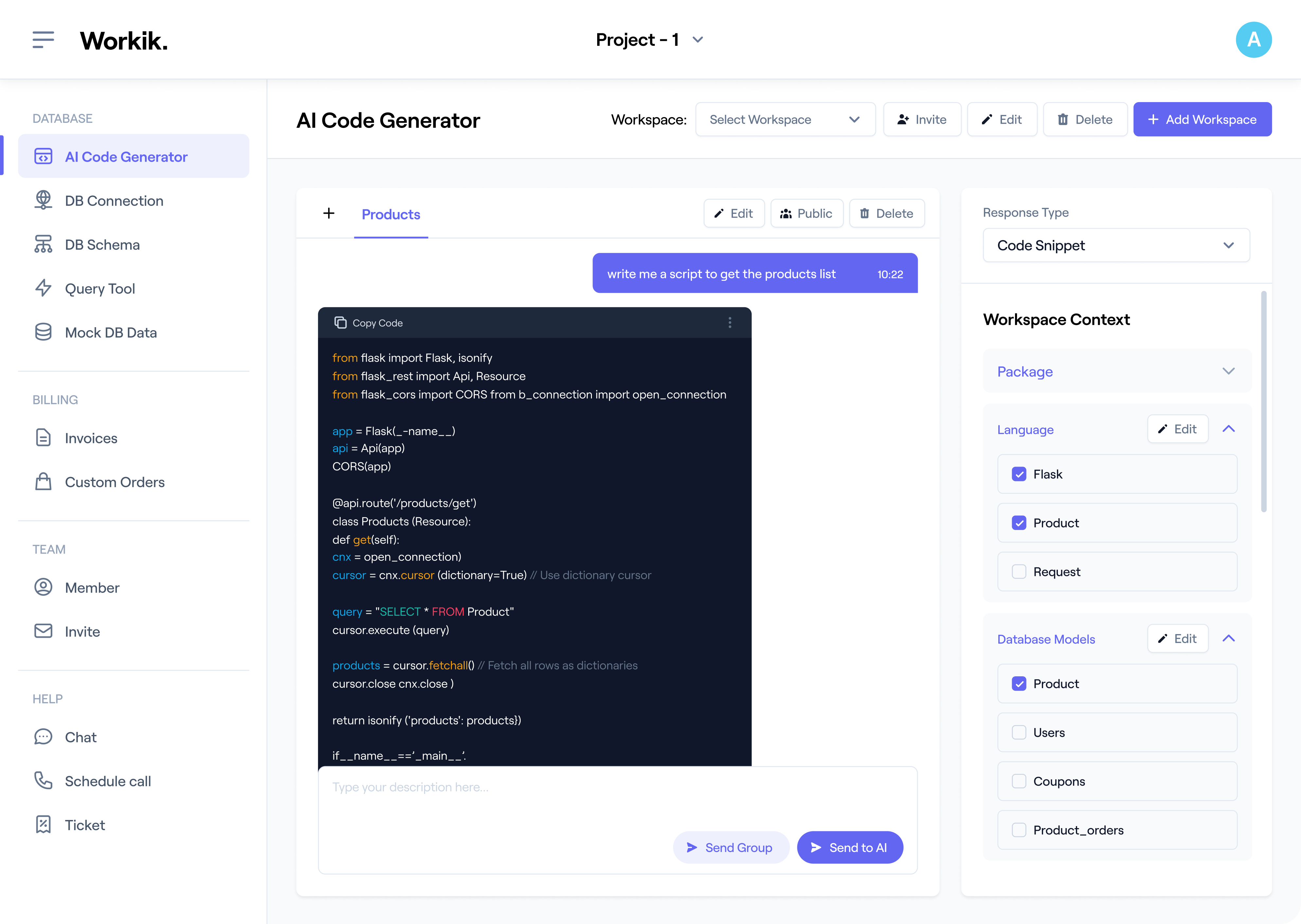
How it works
Sign up in seconds using Google or enter your details manually to access Workik’s AI-powered Security Header tools.
Integrate with GitHub, GitLab, or Bitbucket. Specify frameworks like Node.js, Django, or Spring Boot and define your server type (NGINX, Apache) for precise AI-driven recommendations.
Use AI to generate and optimize Content-Security-Policy and Strict-Transport-Security headers, debug misconfigurations, and fine-tune CORS policies for APIs and multi-tenant setups.
Collaborate with your team in shared workspaces. Use OWASP ZAP or Chrome DevTools to test vulnerabilities and ensure compliance with GDPR and PCI DSS standards.

Expand
.png)
.png)
Expand

Expand


Expand


Expand


Expand


Expand


TESTIMONIALS
Real Stories, Real Results with Workik
Workik’s automated security headers made configuring CSP and HSTS seamless, saving hours on React projects.

Timothy Francis
Frontend Developer
Debugging and fine-tuning CORS headers dynamically was effortless with Workik’s AI tools.

Preston Delgado
Backend Engineer
Implementing strict security headers for APIs was quick and reliable with Workik’s generator.

Lillian Maddox
Full Stack Developer
What are some popular use cases of Workik's AI-powered Security Header Generator?


Workik’s AI-powered Security Header Code Generator is ideal for a wide range of use cases which include but are not limited to:
* Generating Content-Security-Policy and Strict-Transport-Security headers automatically.
* Debugging and optimizing Access-Control-Allow-Origin for APIs.
* Securing React, Angular, and Vue.js apps with dynamic headers.
* Preventing clickjacking using X-Frame-Options on multi-page apps.
* Validating security headers for GDPR and PCI DSS compliance.
* Managing headers across microservices and multi-tenant setups.
What context-setting options are available in Workik’s AI for Security Header Generator?


Workik offers diverse context-setting options for Security Header code assistance by allowing users to:
* Integration with GitHub, GitLab, or Bitbucket for seamless workflows.
* Framework-specific setups for Node.js, Django, Flask, or Spring Boot.
* Custom configurations for NGINX or Apache servers.
* Tailored CORS policies and Access-Control-Allow-Origin for APIs.
* Automated CSP, HSTS, and XSS protection for SPAs and APIs.
* Real-time testing with OWASP ZAP and Chrome DevTools.
How does Workik handle security headers for single-page applications (SPAs)?


Workik dynamically generates security headers tailored for SPAs like those built with React or Angular. For example, it can create a Content-Security-Policy that allows webpack development scripts during testing but restricts them in production. Additionally, it ensures smooth API interactions by fine-tuning Access-Control-Allow-Origin headers to avoid CORS issues.
Can Workik assist in troubleshooting broken headers?


Yes, Workik’s AI debugging pinpoints issues like misconfigured Content-Security-Policy rules that block necessary resources. For example, if your Vue.js app fails to load external stylesheets, Workik identifies the missing style-src directive and provides actionable fixes.
How does Workik secure iframe usage?


Workik configures X-Frame-Options and CSP frame-ancestors to control embedding. For instance, dashboards can be restricted to internal domains, blocking external access to prevent clickjacking.
Can Workik assist with zero-trust models?


Yes, Workik enforces strict CORS policies and CSP rules. For example, it dynamically validates Access-Control-Allow-Origin to allow only authenticated users access to APIs.
Can Workik monitor security headers with analytics tools?


Yes, Workik complements tools like Google Lighthouse, identifying missing or redundant headers and suggesting updates to balance security and performance.
How does Workik handle subdomain security?


Workik’s AI can enforce subdomain-wide security by applying headers like Strict-Transport-Security with the includeSubDomains flag. For instance, if you have app.example.com and api.example.com, Workik ensures all subdomains are secured via HTTPS.
Generate Code For Free

Security Headers: Question and Answer
Security headers are HTTP response headers that enforce security policies between servers and browsers. They prevent attacks like XSS, clickjacking, and data injection. Key headers include Content-Security-Policy (CSP) to restrict resource loading, Strict-Transport-Security (HSTS) for HTTPS enforcement, and X-Frame-Options to prevent iframe-based exploits.
Popular tools for implementing and managing security headers include:
Languages:
JavaScript, Python, PHP, Ruby, Java, C#
Frameworks:
Express.js, Django, Flask, Spring Boot, Ruby on Rails
Servers:
NGINX, Apache, IIS
Testing Tools:
OWASP ZAP, Postman, Mozilla Observatory
Libraries:
Helmet.js (Node.js), django-secure, Flask-Talisman
Security headers are widely used in various scenarios which include but are not limited to:
API Security:
Enforce strict CORS with Access-Control-Allow-Origin.
Preventing XSS:
Restrict scripts using Content-Security-Policy.
Clickjacking Protection:
Block unauthorized iframes with X-Frame-Options.
HTTPS Enforcement:
Ensure secure communication via Strict-Transport-Security.
Session Security:
Protect cookies with Secure and HttpOnly flags.
Compliance:
Validate headers for GDPR and PCI DSS standards.
Microservices:
Apply consistent headers across Kubernetes and Docker.
Third-Party Tools:
Secure Stripe or Google Analytics with CSP rules.
Career opportunities for professionals working with Security Headers include roles such as DevOps Engineer, Web Developer, Frontend Engineer, Cybersecurity Engineer, Site Reliability Engineer, Compliance Specialist, Application Security Consultant, and API Security Specialist.
Workik AI simplifies the implementation and management of security headers by:
Automated Header Generation:
Generate CSP, HSTS, and CORS headers dynamically.
Debugging & Optimization:
Fix misconfigurations in CSP or CORS policies.
Environment Configurations:
Adapt headers for staging, production, or multi-cloud setups.
Validation:
Test headers using OWASP ZAP or Mozilla Observatory.
CI/CD Integration:
Automate header application in GitHub Actions or Jenkins.
Dynamic Adaptation:
Tailor CSP rules for SPAs, SSR frameworks, or APIs.
Cross-Origin Security:
Refine Access-Control-Allow-Origin for secure API workflows.
Refactoring:
Optimize header configurations for better performance and readability.
Documentation:
Auto-generate header documentation for team use and audits.
Explore more on Workik
Get in touch
Don't miss any updates of our product.
© Workik Inc. 2026 All rights reserved.

