Join our community to see how developers are using Workik AI everyday.
Features

Detect Threats Instantly
AI generates signature and behavior-based detection scripts with YARA, VirusTotal, and Scikit-learn for protection.

Scale Detection Effortlessly
Create modular scripts for large-scale monitoring with AI and integrate with Elastic Stack for seamless deployments.

Customize Security Scripts
AI tailors scripts with file hashes, network logs, and APIs, supporting Python, PowerShell, and more.

Refine Logic Accurately
Simulate threats and optimize detection logic using tools like Wireshark and Kali Linux for unmatched accuracy.
How it works
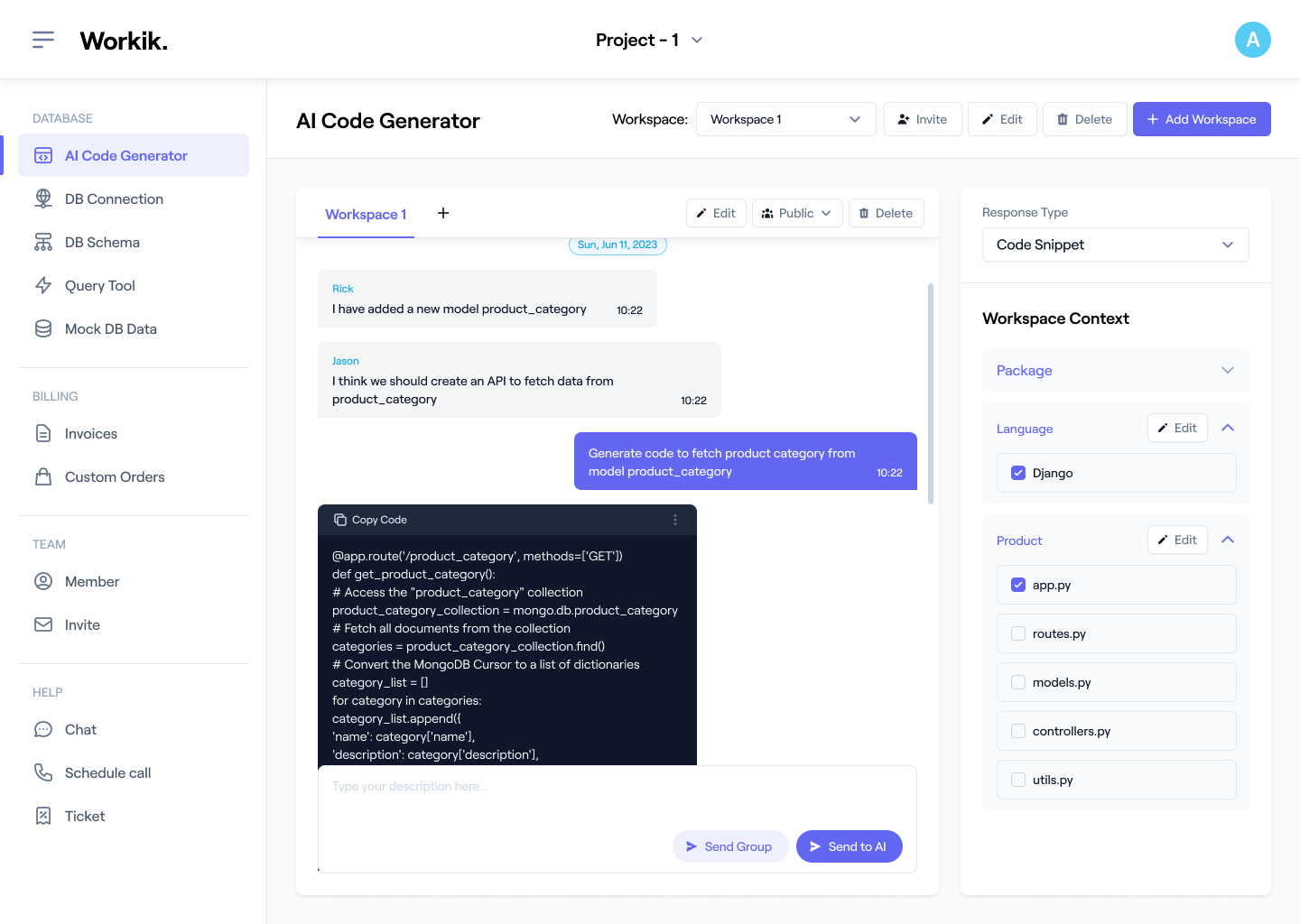
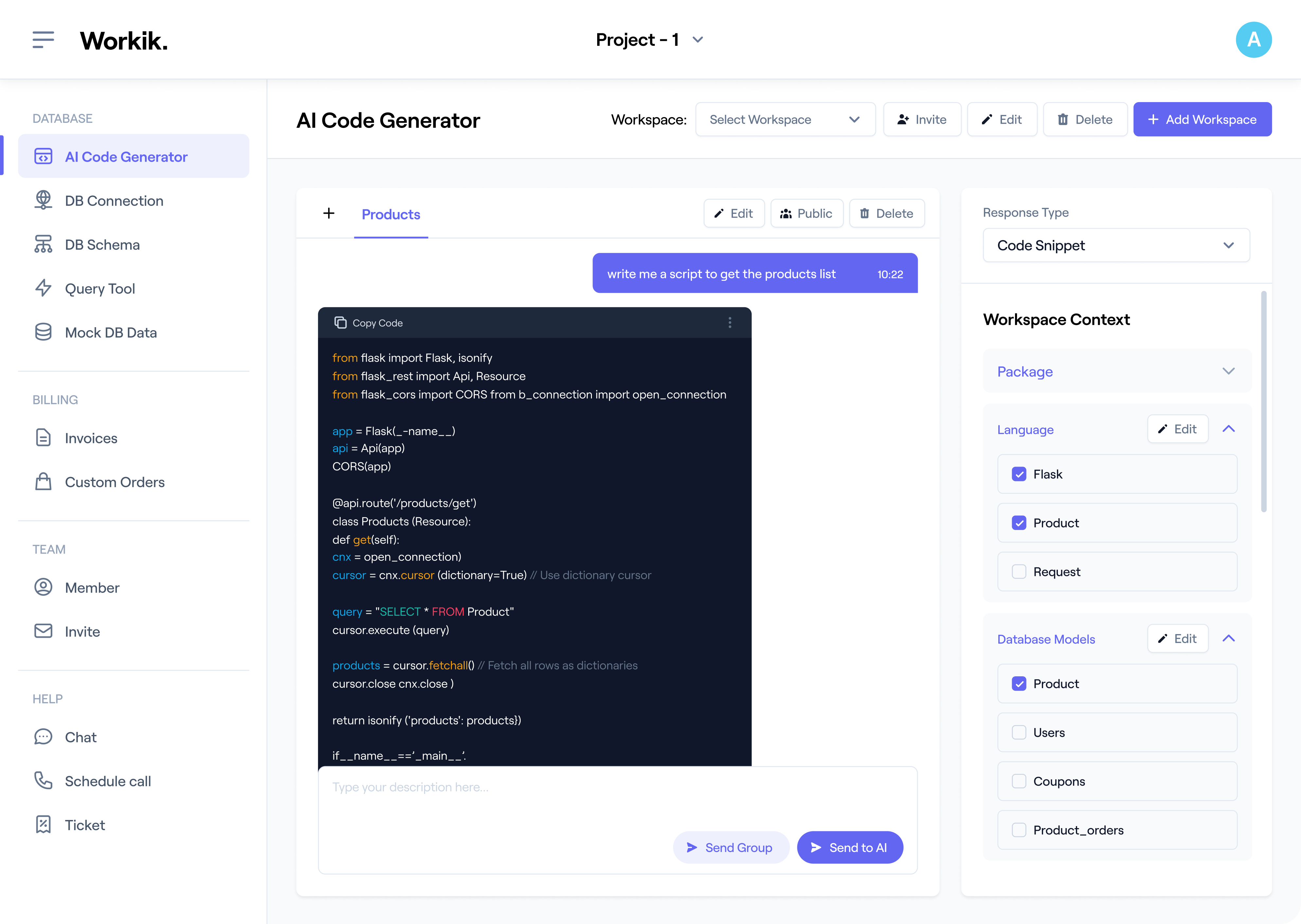
Sign up with Google or enter your details manually to access Workik’s AI-powered Malware Detection tools.
Integrate with GitHub, GitLab, or Bitbucket. Specify frameworks like Scikit-learn or TensorFlow, upload network logs, or define detection methods such as signature-based for AI-tailored script generation.
Use AI to generate and debug malware detection scripts, optimize hash-based scans, fine-tune anomaly detection logic, and refine runtime behavior analysis with tools like VirusTotal and YARA.
Invite your team to review and refine code in shared workspaces. Test with Wireshark and Kali Linux, analyze threats, and optimize detection for scalability.

Expand
.png)
.png)
Expand

Expand


Expand


Expand


Expand


Expand


TESTIMONIALS
Real Stories, Real Results with Workik
Workik’s AI streamlined malware detection by automating signature-based scripts with YARA and VirusTotal.

Glenda Benson
Security Engineer
Workik’s AI tailored precise scripts for runtime behavior detection, improving our threat analysis significantly.

Travis Shields
Senior Software Developer
Integrating Workik with Elastic Stack enhanced our malware detection system's scalability and accuracy.

Adam Beach
DevOps Engineer
What are some popular use cases of Workik's AI-powered Malware Detection Script Generator?


Workik’s AI-powered Malware Detection Script Generator is ideal for a wide range of use cases which include but are not limited to:
* Generate signature-based scripts using YARA for detecting known threats.
* Build behavior-based detection logic to monitor runtime anomalies.
* Automate traffic analysis with Wireshark for detecting unauthorized access.
* Optimize malware detection algorithms to reduce false positives.
* Simulate real-world attacks using Kali Linux to test detection scripts.
* Create modular scripts for large-scale malware monitoring with Elastic Stack.
* Automate hash-based malware scanning with tools like VirusTotal.
* Develop scripts to detect file tampering or unauthorized modifications.
* Create customized alerts for malware-triggered network events.
What context-setting options are available in Workik’s AI for Malware Detection Script Generator?


Workik offers diverse context-setting options for malware detection assistance by allowing users to:
* Link repositories from GitHub, GitLab, or Bitbucket for seamless integration.
* Choose Python, PowerShell, or C++ for tailored malware scripts.
* Define detection methods like signature-based, heuristic, or behavioral analysis.
* Integrate threat intelligence tools like VirusTotal or OpenIOC.
* Upload network logs or database schemas for anomaly detection.
* Add runtime behavior patterns for advanced malware detection.
* Set specific thresholds for anomaly detection using AI-driven logic.
* Integrate with security frameworks like Elastic Stack or Suricata.
* Include file hash databases for automating malware signature matching.
Can Workik generate scripts for detecting zero-day vulnerabilities?


Yes, Workik’s AI helps craft behavior-based scripts using advanced heuristics to monitor patterns like privilege escalation, memory manipulation, or unauthorized network access, enabling early detection of zero-day vulnerabilities.
How does Workik handle evolving malware tactics?


Workik’s AI adapts to advanced malware evasion techniques such as code obfuscation, polymorphism, and sandbox evasion by generating scripts with dynamic behavior analysis and real-time threat adaptation.
Can Workik create scripts for encrypted traffic analysis?


Yes, Workik generates scripts that leverage metadata inspection, TLS fingerprinting, and machine learning models to identify malicious patterns in encrypted network traffic without decrypting sensitive data.
Is Workik useful for compliance-related malware detection?


Yes, Workik generates scripts aligned with regulatory frameworks like GDPR, HIPAA, and PCI DSS, ensuring malware detection systems meet stringent compliance standards through tailored security policies.
Can Workik create scripts for IoT malware detection?


Workik’s AI generates scripts specifically for IoT environments, focusing on lightweight anomaly detection for MQTT protocols, firmware validation, and monitoring device-to-device communication for malicious behavior.
Generate Code For Free

Malware: Question and Answer
Malware, short for malicious software, is any program or file intentionally designed to harm, exploit, or compromise systems, networks, or devices. It includes viruses, ransomware, spyware, worms, and trojans. Malware often spreads through phishing, drive-by downloads, or infected applications and is used for data theft, system disruption, or unauthorized access.
Key technologies in malware detection include:
Languages:
Python, PowerShell, C++, Go
Frameworks:
Elastic Stack, Snort, Suricata
Libraries:
Scikit-learn, TensorFlow, Pyshark
Tools:
Wireshark, YARA, VirusTotal, Kali Linux
APIs:
VirusTotal API, Hybrid Analysis
Testing Platforms:
Cuckoo Sandbox, Metasploit Framework
Popular applications of malware detection include but are not limited to:
Endpoint Security:
Real-time protection against ransomware and trojans.
Network Intrusion Detection:
Detect suspicious traffic with tools like Suricata.
File Integrity Monitoring:
Identify tampered files using hash-based scans via YARA.
Threat Intelligence:
Match malware signatures using platforms like VirusTotal.
IoT Security:
Monitor devices for unauthorized activity or firmware changes.
Cloud Security:
Scan cloud environments for malware with APIs like Hybrid Analysis.
Career opportunities for professionals working with Malware Detection include roles such as Cybersecurity Engineer, Malware Analyst, SOC Analyst, Threat Hunter, Red Team Specialist, and DevSecOps Engineer.
Workik AI streamlines malware detection tasks by:
Script Generation:
Generate signature or behavior-based detection scripts with YARA and VirusTotal.
Threat Analysis:
Automate runtime behavior and network anomaly detection using Wireshark.
Refactoring and Optimization:
Refine detection logic, reduce false positives, and enhance script performance.
API Integration:
Access real-time threat intelligence via VirusTotal API.
Testing and Debugging:
Test and debug detection scripts in Kali Linux sandboxes.
Scalability:
Build modular scripts for large-scale monitoring with Elastic Stack.
Documentation:
Automate detailed reports for malware detection workflows.
Explore more on Workik
Get in touch
Don't miss any updates of our product.
© Workik Inc. 2026 All rights reserved.

