Join our community to see how developers are using Workik AI everyday.
Supported AI models on Workik
GPT 5.2, GPT 5.1 Codex, GPT 5.1, GPT 5 Mini, GPT 5, GPT 4.1 Mini
Gemini 3 Flash, Gemini 3 Pro, Gemini 2.5 Pro, Gemini 2.5 Flash
Claude 4.5 Sonnet, Claude 4.5 Haiku, Claude 4 Sonnet, Claude 3.5 Haiku
Deepseek Reasoner, Deepseek Chat, Deepseek R1(High)
Grok 4.1 Fast, Grok 4, Grok Code Fast 1
Models availability might vary based on your plan on Workik
Features

Tailored Authentication
Easily customize login workflows with multi-factor, social, & biometric options for superior security.

API Integration
Automate secure API connections to user databases and services, enhancing scalability and reliability.

Security Analytics
Access real-time insights for immediate threat detection and response, optimizing login security.

Code Optimization
Achieve peak performance with AI enhanced code reviews, ensuring top-tier security standards.
How it works
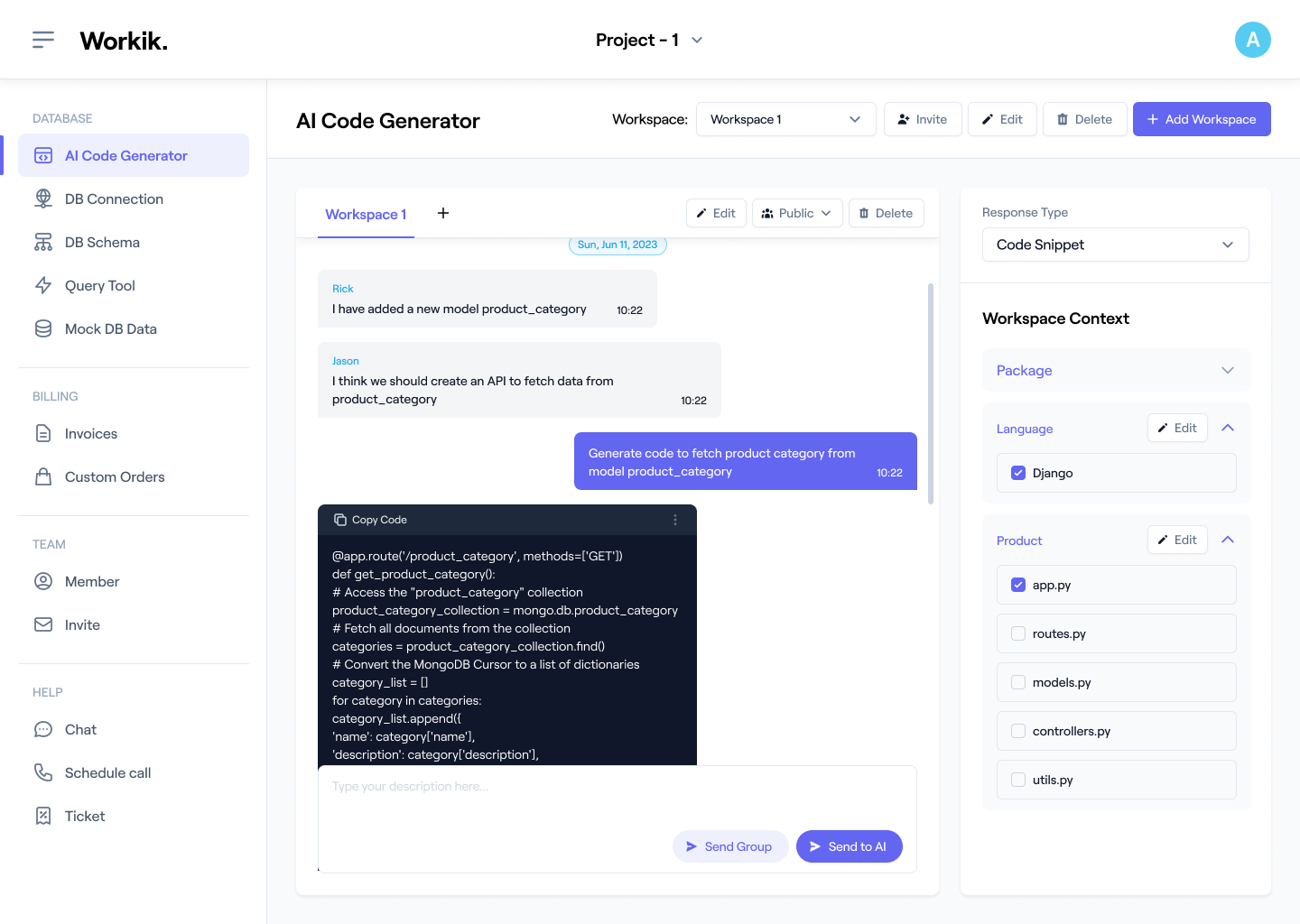
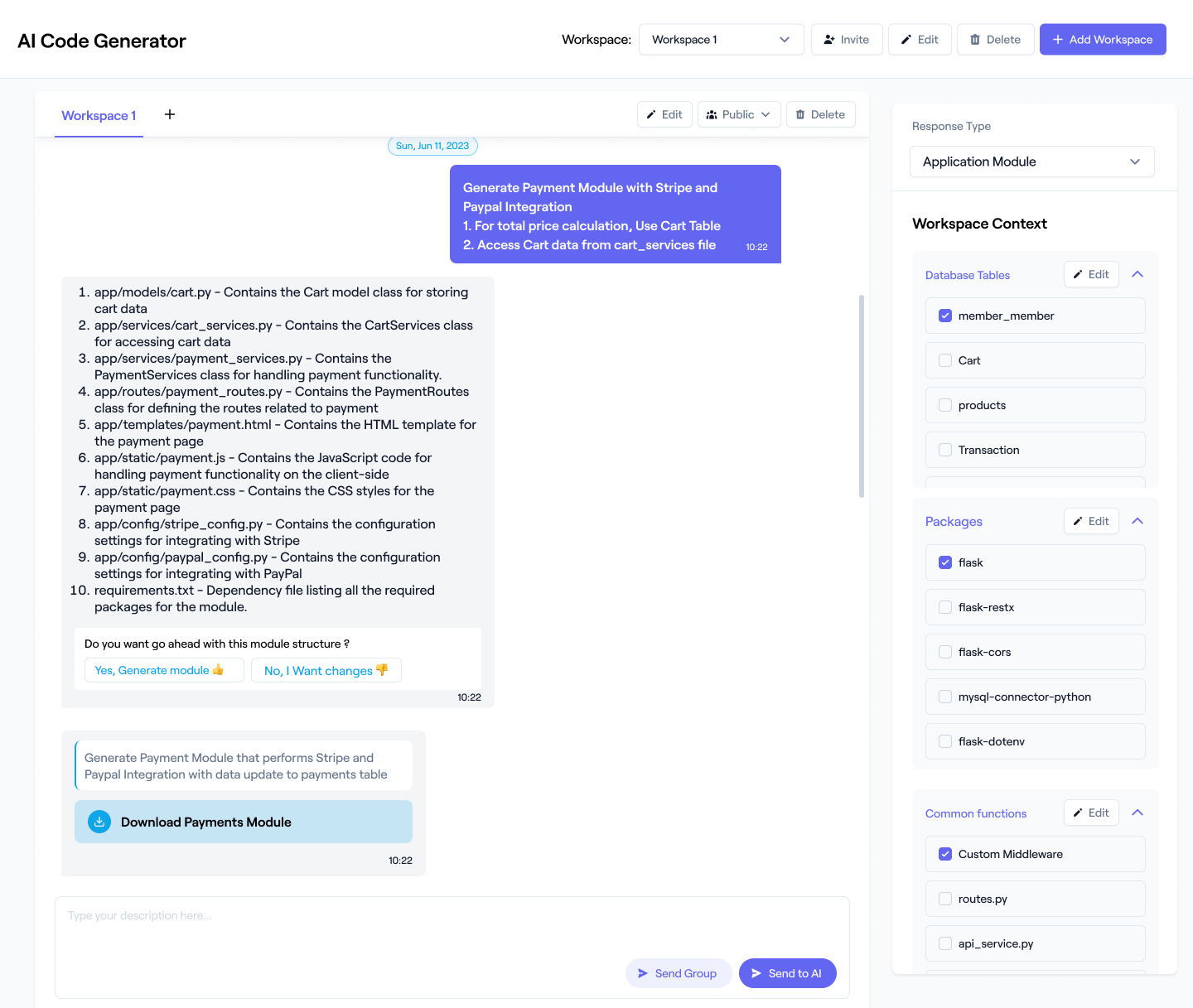
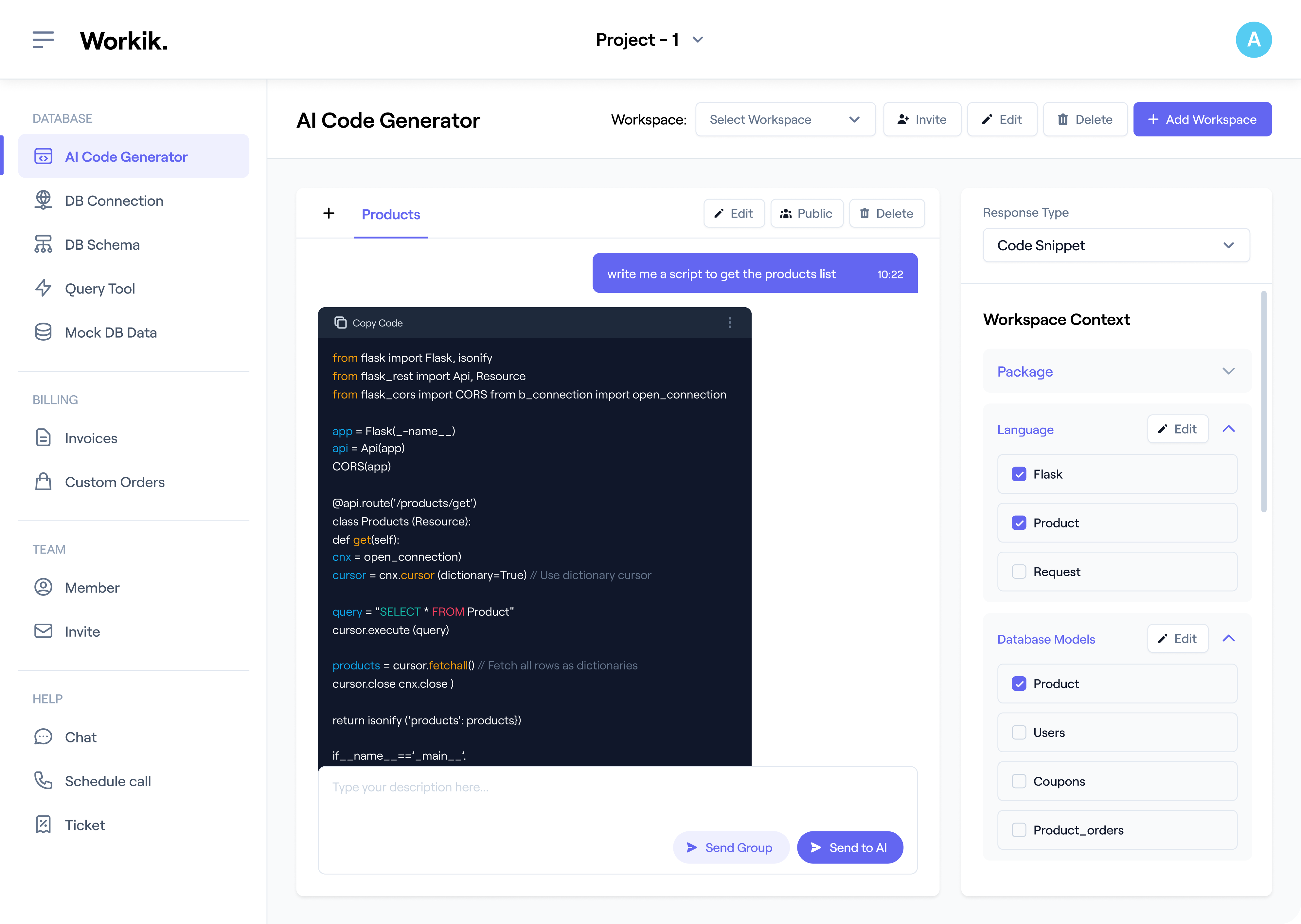
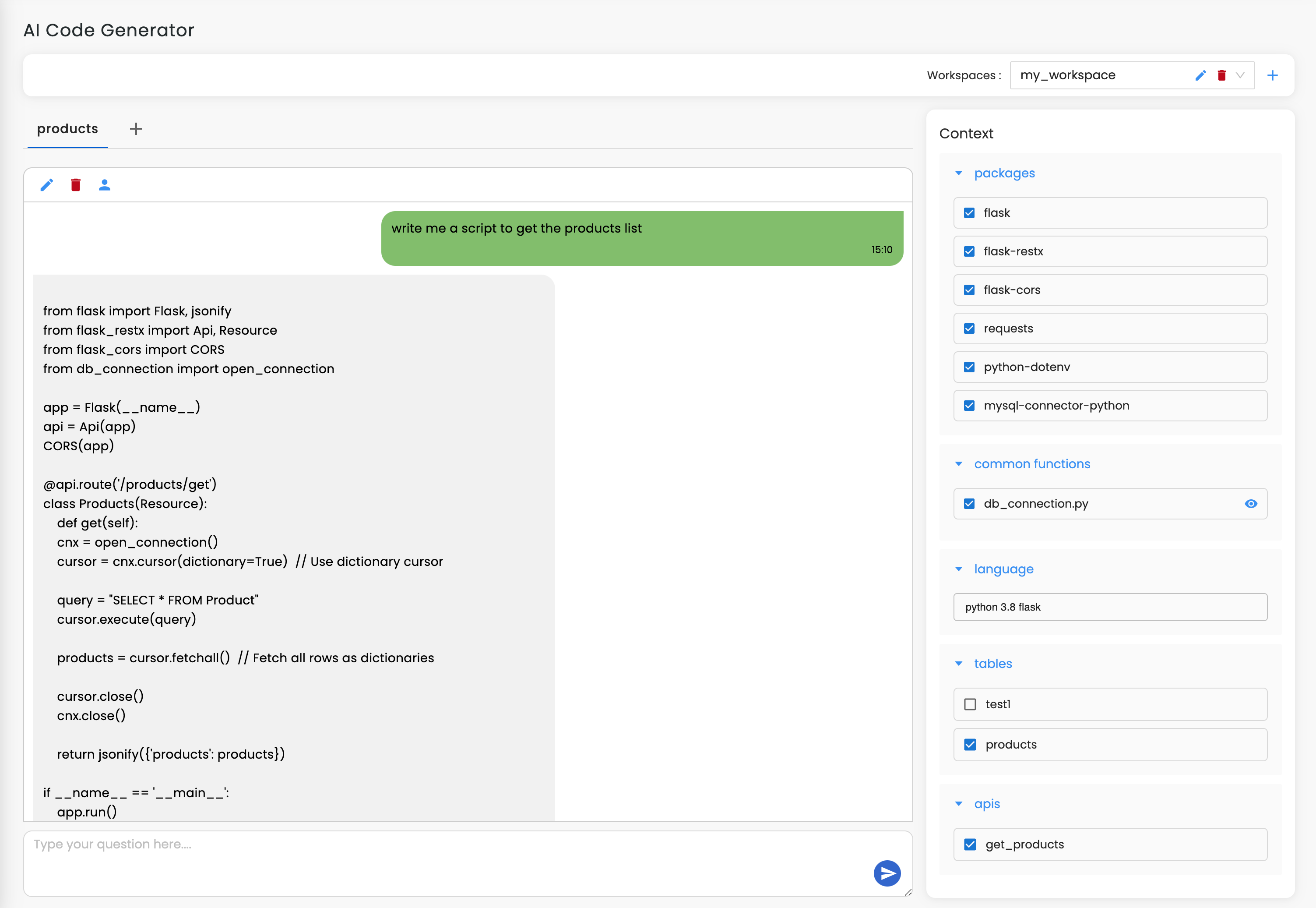
Begin your journey by signing up on Workik either through Google or by entering your details manually and you are ready to use AI for Login Authentication.
This step is completely optional. Choose your preferred languages and frameworks, specify the security protocols you need, add database schema, or integrate with Github, Gitlab, or Bitbucket. Workik’s AI adapts to your specifications.
Get complete assistance from AI. It analyzes your requirements, applies best security practices, and generates efficient authentication systems according to your preference.
Bring your team for a collaborative workspace. Automate repetitive aspects of the authentication process using Workik's AI-driven workflow pipelines.
supercharge development
Try For Free

FEATURES

Implement cutting-edge security measures, like behavioral biometrics.

Streamline complex authentication workflows with AI automation.

Benefit from AI's ability to predict and block fraudulent login attempts.

Leverage anomaly detection algorithms to identify and mitigate security risks.

Generate customized security questions using AI, providing a personalized layer of user security.
Try For Free

FEATURES

Simplify the creation of secure login systems with AI.

AI Facilitates smooth integration with existing projects or databases.

Design user-friendly login processes with AI, improving the end-user experience.

Learn to scale your authentication system with insights from AI.

Seamlessly incorporate authentication code into existing projects.

Expand

Expand

Expand


Expand

Expand


Expand


Expand


TESTIMONIALS
Real Stories, Real Results with Workik
AI-generated OAuth and JWT setups exceeded quality & security expectations, saving weeks of development.

Mia Zhang
Full Stack Developer
The anomaly detection feature is outstanding. We were able to identify & mitigate potential security breaches before they happened.

Chris Matthews
Cybersecurity Analyst
The AI's ability to automate security testing within our CI/CD pipeline has been phenomenal. It's like having an extra set of eyes ensuring our login systems are secure.

Jordan Liu
DevOps Engineer
What are some of the popular Workik's Login Authentication Code Generator use cases?


Workik's Login Authentication Code Generator is widely used for a range of applications:
1. Quickly set-up secure, SMS or email-based OTP systems.
2. Implement JWT or OAuth tokens for stateless and secure API access.
3. Incorporate fingerprint or facial recognition for advanced security.
4. Dynamically adjust authentication strength based on user behavior & login patterns
5. Facilitate SSO across different applications for enhanced user experience.
6. Generate code that helps meet GDPR, HIPAA, or other compliance requirements.
What type of context can I add in Workik?


While adding context in Workik is optional, it enhances the AI's understanding for personalized output. For Login authentication requirements, you can specify:
1. Application Type (web, mobile, desktop)
2. User Base Size (small-scale to enterprise)
3. Security Protocols (SSL, TLS, encryption)
4. Database Integration (MySQL, MongoDB)
5. API Specifications (REST, GraphQL)
6. Third-Party Services (OAuth providers, external databases)
Can AI handle advanced security features like biometric authentication?


Yes, It enables the integration of fingerprint, facial recognition, and other biometric data for user verification, providing an additional layer of security. It simplifies the complex coding required for biometric systems, making it accessible for developers of varying skill levels.
Is it possible to integrate the generated code with existing databases and user management systems?


Yes, the code generated can be easily integrated with various databases and user management systems, allowing for a seamless addition of secure login functionality to your existing infrastructure.
In what ways can the AI assist with multi-factor authentication setups?


The tool supports the integration of various multi-factor authentication methods, including SMS-based OTPs, email verification, and biometric authentication, providing an extra layer of security.
How does the collaborative workspace in Workik help teams?


Workik's workspaces offer a shared environment where teams can jointly develop and refine login authentication code. This setup facilitates seamless collaboration, allowing for shared codebases, real-time reviews, and collective testing, leading to efficient and secure authentication solutions.
Can't find answer you are looking for?
Request question

Request question
Please fill in the form below to submit your question.
Generate Code For Free

Login AUthentication Code Question & ANSWER
Login authentication code typically refers to the code required to verify user credentials when they attempt to access a secure system or application. It is crucial for securing applications and managing user access. It involves various components such as user authentication, session management, token-based authentication, password encryption, and role-based access control.
Popular frameworks and libraries used in writing Login Authentication Code are:
1. JavaScript (Node.js):
Passport.js, bcrypt, JWT (jsonwebtoken)
2. Python (Flask/Django):
Flask-Login, Django-Auth, PyJWT
3. Java (Spring Boot):
Spring Security, JWT, BCrypt
4. Ruby on Rails:
Devise, OmniAuth, JWT
5. PHP:
Laravel Passport, PHP-JWT, bcrypt
6. C# (.NET):
ASP.NET Identity, JWT, BCrypt
Popular use cases of Login Authentication Code include:
1. User Authentication:
Implementing login functionality for web and mobile applications.
2. Session Management:
Managing user sessions and maintaining login states.
3. Token-Based Authentication:
Using JWT for stateless authentication.
4. Password Encryption:
Encrypting user passwords for secure storage.
5. Role-Based Access Control:
Implementing access controls based on user roles.
Career opportunities and technical roles available for professionals in writing Login Authentication Code include Backend Developer, Full-Stack Developer, Security Engineer, DevOps Engineer, Mobile Developer and more.
Workik AI provides broad Login Authentication code assistance, which includes:
1. Code Snippet Generation:
Produces authentication code snippets for various languages and frameworks.
2. Debugging:
Identifies and fixes issues in authentication code with intelligent suggestions.
3. Optimization:
Recommends best practices for secure and efficient authentication mechanisms.
4. Security:
Provides guidelines for secure password storage and handling sensitive information.
5. Token Management:
Helps in implementing and managing JWT and other token-based authentication methods.
6. Documentation:
Generates comprehensive documentation for authentication APIs and workflows.
7. Error Handling:
Suggests best practices for handling authentication errors and exceptions.
Explore more on Workik
Get in touch
Don't miss any updates of our product.
© Workik Inc. 2026 All rights reserved.

