Join our community to see how developers are using Workik AI everyday.
Features

Streamline IP Blocklists
Use AI to generate IP blocklists by analyzing traffic patterns and suspicious behavior with IPTables or NGINX.

Optimize Firewall Rules
AI fine-tunes blacklisting rules, removing redundancies and improving efficiency for tools like ModSecurity or Cloudflare.

Seamless System Integration
Export AI-generated configs in JSON or YAML for quick deployment to AWS WAF or similar systems.

Dynamic Threat Detection
Leverage AI to block malicious IPs dynamically using Suricata and Snort for alerts and responses.
How it works
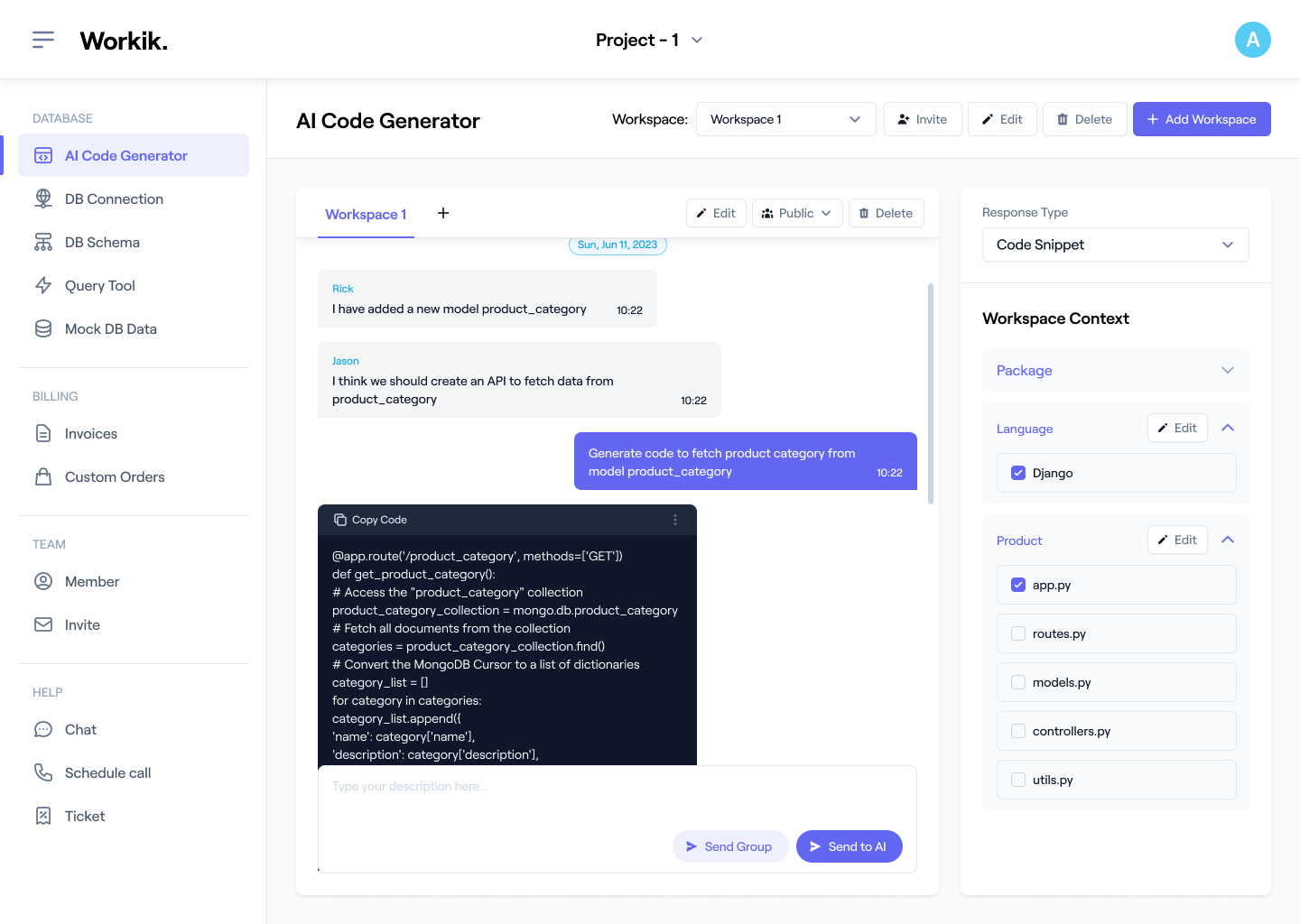
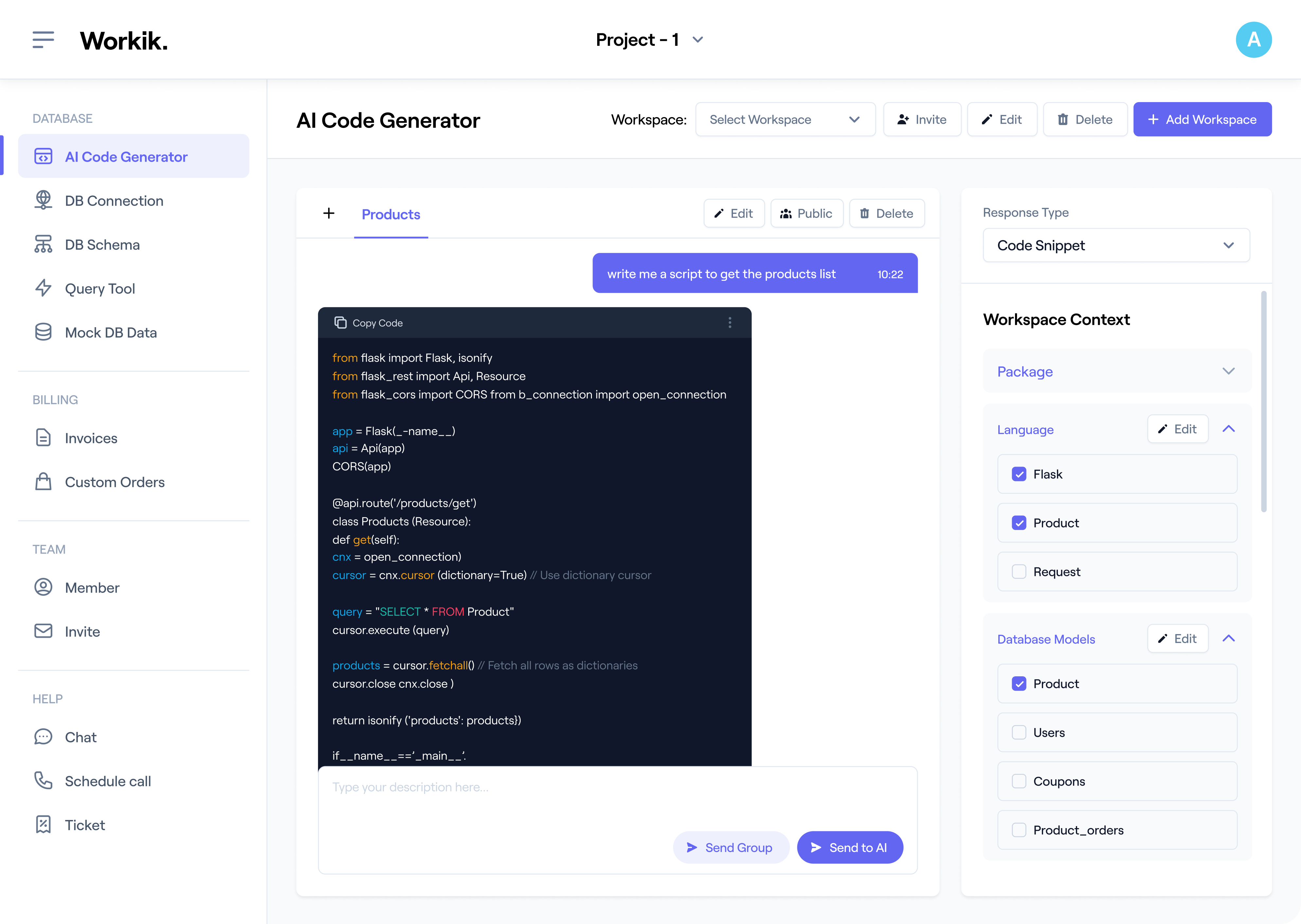
Sign up using Google or manual credentials to unlock Workik AI for seamless IP blacklisting code generation.
Link repositories from GitHub, GitLab, or Bitbucket. Provide malicious IP lists, traffic logs, or firewall configurations, and specify tools like NGINX or Cloudflare for customized AI support.
Use AI for optimized IP blocking rules, whitelists, and blacklists. Whether generating a blocklist for DDoS prevention or refining rules for firewall systems, AI accelerates the process.
Invite your team to collaborate on projects within Workik. Share workspaces, assign tasks, and use AI to analyze rule effectiveness, optimize configurations, and enhance system security.

Expand
.png)
.png)
Expand

Expand


Expand


Expand


Expand


Expand


TESTIMONIALS
Real Stories, Real Results with Workik
Workik AI simplified DDoS protection and firewall tuning in minutes!

Sarah Timmons
Network Security Engineer
With Workik AI, I generated rules compatible with our outdated framework instantly!

Ravi Patel
Senior Software Developer
Workik AI helped my team secure our APIs with dynamic IP blocking. It was a game-changer!

Amanda Lee
DevOps Specialist
What are the popular use cases of Workik AI for IP Blacklisting Code Generation?


Some popular use cases of Workik AI for IP Blacklisting Code Generation for developers include but are not limited to:
* Generate tailored IP blocklists and whitelists based on traffic patterns or suspicious activity.
* Create and deploy firewall rules for tools like IPTables or ModSecurity.
* Integrate with platforms such as AWS WAF or Cloudflare for enhanced security measures.
* Configure dynamic IP blocking for real-time threat response.
* Implement access control policies to prevent unauthorized connections.
* Refine blacklisting rules with AI insights to enhance efficiency and reduce redundancy.
* Set up test environments for simulated malicious traffic to evaluate rule performance.
What kind of context can I add in Workik AI related to my IP Blacklisting project?


Setting context in Workik is optional but enhances AI responses for your IP Blacklisting projects. Here are the types of context you can add:
* Add traffic logs, malicious IP lists, or known threat patterns.
* Specify programming languages such as Python, Bash, or PHP for tailored code assistance.
* Mention firewall tools like IPTables, NGINX, or Fail2Ban to align configurations.
* Add database schemas like MySQL or PostgreSQL for seamless backend integration.
* Specify security policies or configurations in JSON or YAML for accurate AI-driven rule creation.
How can Workik AI help manage region-specific IP blocking rules?


Workik AI helps manage by analyzing geolocation data. For example, you can block traffic from high-risk regions while ensuring access for trusted areas. This is particularly useful for compliance with region-specific regulations or to mitigate geographically targeted cyberattacks.
Can Workik AI assist in creating time-bound IP blacklists?


Yes, Workik AI can generate time-based IP blocking rules, perfect for scenarios like temporarily blocking malicious traffic during a DDoS attack or granting limited-time access for maintenance purposes. The AI dynamically adjusts blocklists to meet specific time constraints, reducing manual overhead.
How does Workik AI optimize integration with hybrid infrastructures?


Workik AI seamlessly integrates with on-premise firewalls and cloud platforms like AWS or Azure. For instance, it can synchronize blocklists between a local IPTables setup and a cloud-based WAF, ensuring consistent security across systems.
Can Workik AI detect and block patterns in evolving threats?


Absolutely. Workik AI uses machine learning to identify patterns like repeated failed login attempts or unusual data requests. For example, it can block a botnet probing for vulnerabilities by recognizing anomalies in access patterns before they escalate into an attack.
How does Workik AI help test the effectiveness of IP blocking rules?


Workik AI enables simulated threat scenarios, like emulating botnet traffic or spoofing IPs, to evaluate the robustness of your blocklists. For instance, you can test if specific IPs bypass rules or if legitimate traffic is unintentionally blocked, ensuring both security and functionality.
Generate Code For Free

IP Blacklisting: Question and Answer
IP blacklisting is a security measure that blocks access from specific IP addresses identified as malicious or suspicious. It helps protect systems by filtering unauthorized traffic, preventing DDoS attacks, stopping brute force attempts, and safeguarding sensitive data.
Popular tools and frameworks for IP blacklisting include:
Firewall Management:
IPTables, Fail2Ban, ModSecurity
Cloud Platforms:
AWS WAF, Azure Firewall
Threat Analysis:
Suricata, Snort
Configuration Formats:
JSON, YAML for rulesets
Geolocation Blocking:
Cloudflare, MaxMind GeoIP
Popular use cases of IP blacklisting include:
Enterprise Security:
Protect internal networks from unauthorized external access.
API Protection:
Block malicious IPs targeting API endpoints.
E-commerce Security:
Prevent bots from scraping prices or launching credential stuffing attacks.
DDoS Mitigation:
Block IPs from high-frequency, suspicious traffic sources.
Spam Prevention:
Prevent spam or phishing attempts by blocking known malicious IP ranges.
IoT Device Protection:
Safeguard smart devices from botnets or unauthorized access.
Access Restrictions:
Enforce role-based access by blocking IPs outside of specific IP ranges.
Roles involving IP blacklisting include Network Security Engineer, Cybersecurity Specialist, DevOps Engineer, and Backend Developer. Other roles include Threat Analyst, Firewall Administrator, and Infrastructure Security Architect.
Workik AI enhances IP blacklisting by:
Rule Creation:
Generate optimized rules for IPTables or ModSecurity.
Dynamic Updates:
Automate blocklist updates using real-time traffic patterns.
Geolocation Filtering:
Create region-specific blocklists to mitigate targeted threats.
Testing:
Simulate attack scenarios to validate blocking rules.
Legacy System Support:
Generate rules compatible with older firewalls or configurations.
Behavioral Analysis:
Identify suspicious IP behavior like repeated failed logins or unusual traffic spikes and block accordingly.
Performance Optimization:
Analyze and refine rules to reduce latency and improve firewall efficiency.
Threat Visualization:
Generate graphical insights into blocked traffic for better monitoring and reporting.
Collaboration:
Enable teams to share and refine IP blocklists within unified workspaces.
Seamless Deployment:
Export configurations in JSON or YAML formats for direct integration into firewalls or cloud platforms like AWS WAF.
Explore more on Workik
Get in touch
Don't miss any updates of our product.
© Workik Inc. 2026 All rights reserved.

