Join our community to see how developers are using Workik AI everyday.
Features

Enhance Threat Detection
AI detects anomalies and generate SIEM-compatible alerts for Splunk and QRadar using TensorFlow.

Visualize Security Insights
AI helps create actionable dashboards with Matplotlib and Plotly, highlighting critical threat metrics and patterns.

Generate Custom IDS Rules
AI crafts Snort and Suricata rules based on traffic analysis, updating configurations dynamically.

Optimize Detection Code
Debug and refactor detection scripts with AI for frameworks like OpenSSL and Nmap.
How it works
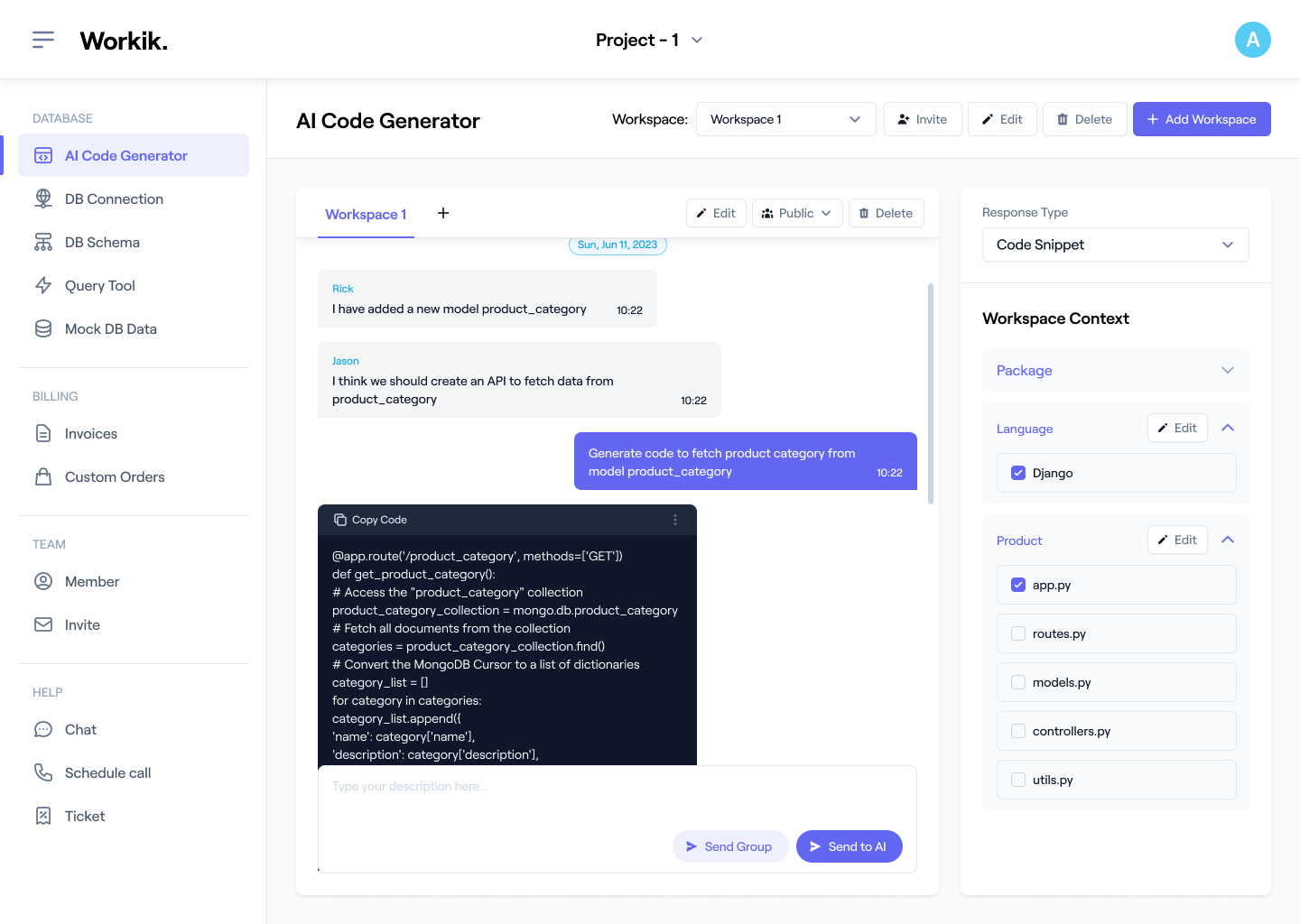
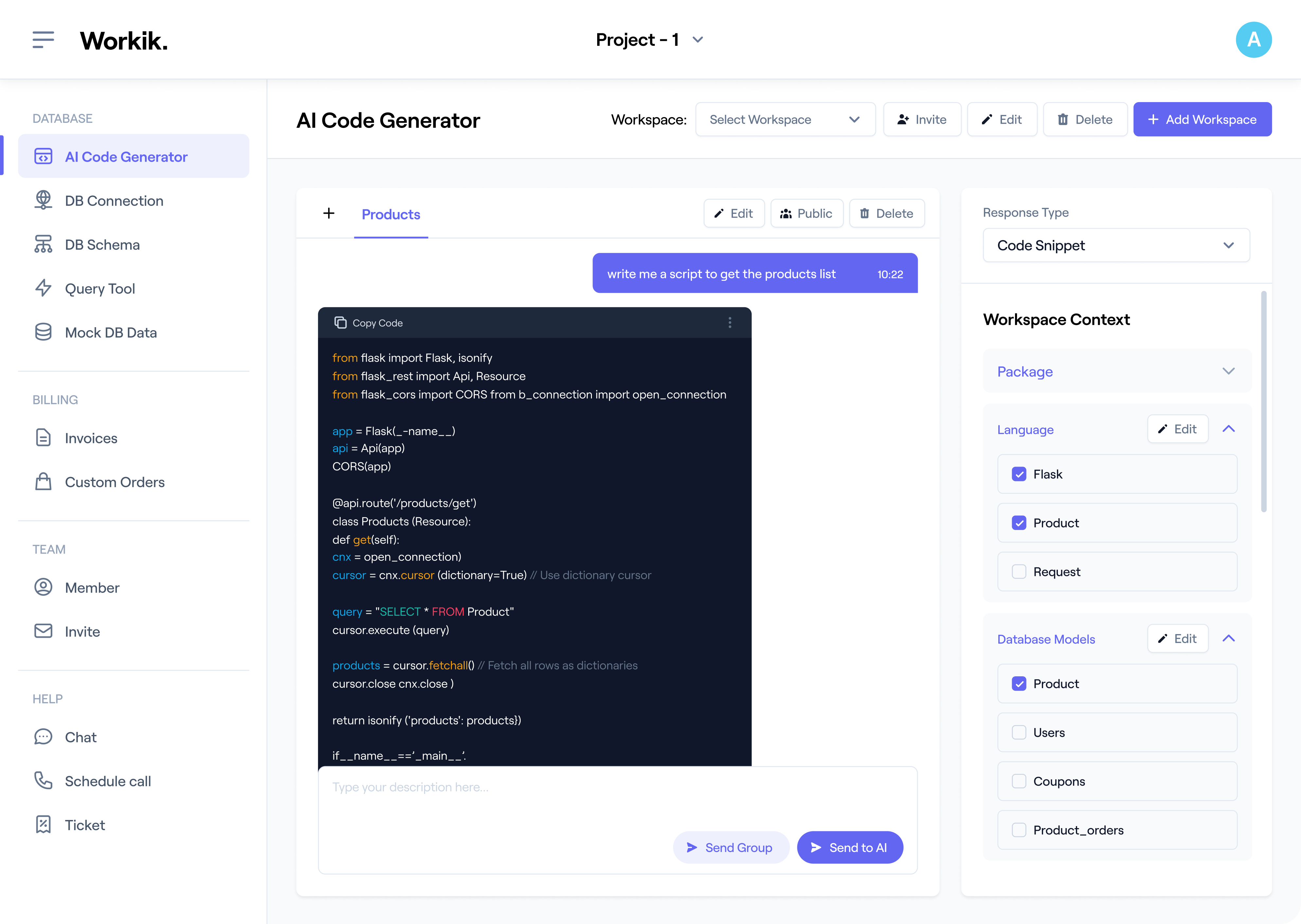
Sign up in seconds using Google or manually enter your details to access Workik’s AI-powered threat detection tools.
Link repositories from GitHub, GitLab, or Bitbucket. Add relevant intrusion detection systems, database schemas, and security protocols for precise AI support tailored to your needs.
Generate custom rules, create scripts for anomaly detection, or generate security configurations. Whether managing real-time traffic or building defensive APIs, AI ensures faster, smarter solutions.
Invite your team to collaborate on workflows within Workik. Share workspaces, review generated code, and leverage AI insights to enhance threat detection and response strategies.

Expand
.png)
.png)
Expand

Expand


Expand


Expand


Expand


Expand


TESTIMONIALS
Real Stories, Real Results with Workik
Workik AI saved hours by generating IDS rules instantly for our projects.

Chris Steele
Senior Security Engineer
As a junior dev, I quickly built threat models with AI-guided TensorFlow support.

Alex Carter
Junior Software Developer
AI-powered dashboards helped us spot vulnerabilities and strengthen defenses fast.

Priya Desai
Lead DevOps Engineer
What are some popular use cases of Workik AI-powered Threat Detection Code Generator?


Some popular use cases of Workik AI-powered Threat Detection Code Generator for developers include but are not limited to:
* Create intrusion detection rules for tools like Snort and Suricata.
* Generate machine learning models for anomaly detection in network traffic.
* Integrate with SIEM systems like Splunk for threat alert management.
* Create security scripts for vulnerability scanning using frameworks like OpenSSL.
* Visualize threat patterns with data from Plotly or Matplotlib dashboards.
* Optimize detection logic for handling large-scale traffic without performance bottlenecks.
* Generate adaptive responses for evolving threats based on AI-driven insights.
What context-setting options are available in Workik AI for Threat Detection Code Generation?


Workik offers several context-setting options to tailor threat detection code generation, allowing users to:
* Integrate repositories from GitHub, GitLab, or Bitbucket into your codebases.
* Add IDS configurations like Snort rules, Suricata YAML files, and security protocols.
* Define real-time data inputs such as network traffic logs or packet captures (PCAP).
* Upload API blueprints to monitor security alerts and responses dynamically.
* Specify TensorFlow models or libraries like PyTorch for custom anomaly detection.
* Configure dynamic parameters like IP ranges, threat levels, and detection thresholds.
* Set up security-specific rate limits and logging preferences for detection rules.
Can Workik AI assist in regulatory compliance for security standards?


Yes, Workik AI helps by generating rule sets and scripts aligned with compliance requirements like PCI DSS or GDPR. For example, it can create scripts that log user data access attempts, aiding in forensic analysis and ensuring regulatory adherence.
How can Workik AI help prevent zero-day attacks?


AI models trained on historical data can identify unusual traffic patterns that might indicate zero-day vulnerabilities. For example, it generates scripts to detect traffic spikes from unknown origins and blocks them proactively.
Can Workik AI assist with proactive threat hunting?


Yes, Workik AI analyzes logs and generates hunting queries tailored for tools like Splunk or Elasticsearch. For instance, it creates queries to detect lateral movement or unauthorized access within internal networks.
How does Workik AI enhance response to evolving attack methods?


Workik AI dynamically updates IDS rules and detection scripts based on threat intelligence feeds. For example, it can integrate with MISP (Malware Information Sharing Platform) to adapt detection strategies for newly identified malware families.
Generate Code For Free

Threat Detection: Question and Answer
Threat detection involves identifying and mitigating security risks in systems and networks by analyzing patterns, behaviors, and anomalies. It leverages technologies like intrusion detection systems (IDS), anomaly detection algorithms, and AI to safeguard data and infrastructure from cyber threats, ensuring system integrity and compliance.
Popular frameworks and libraries used in threat detection include:
IDS and IPS Tools:
Snort, Suricata
Anomaly Detection:
TensorFlow, PyTorch
Log Analysis:
ELK Stack (Elasticsearch, Logstash, Kibana)
Visualization:
Matplotlib, Plotly
SIEM Systems:
Splunk, IBM QRadar
Data Parsing:
Scapy, Wireshark
Popular use cases of threat detection include:
Banking Systems:
Monitor transactions for fraudulent activities and detecting unusual access patterns.
E-commerce Platforms:
Identify bot attacks or unauthorized login attempts by analyzing traffic anomalies.
Healthcare Systems:
Secure patient data by detecting and blocking unauthorized access attempts.
Cloud Environments:
Ensure compliance by monitoring API usage and identify potential misconfigurations or abuse of cloud services.
Smart Grids:
Detect anomalies in energy consumption or communication patterns to prevent cyberattacks on infrastructure.
Telecommunications:
Secure networks from Distributed Denial-of-Service (DDoS) attacks.
Career opportunities and technical roles in threat detection include Security Analyst, Threat Intelligence Analyst, Network Security Engineer, Cybersecurity Specialist, Machine Learning Engineer, DevSecOps Engineer, Incident Response Specialist, and Cloud Security Architect (threat detection-focused).
Workik AI provides end-to-end assistance in threat detection code generation by:
Rule Creation:
IDS rule generation for Snort and Suricata based on network traffic analysis.
ML Model Development:
Building anomaly detection models using TensorFlow and PyTorch.
Code Debugging:
Identifying and resolving issues in detection logic for optimal performance.
Data Analysis:
Generating queries for Splunk and ELK Stack to monitor logs and traffic.
Visualization:
Creating dashboards with Plotly or Matplotlib to display actionable insights.
Response:
Generating scripts for dynamic incident responses and mitigation actions.
Performance Optimization:
Enhancing detection system efficiency by streamlining code and configurations.
Regulatory Compliance:
Assisting in generating detection rules that align with standards like PCI DSS and GDPR.
Explore more on Workik
Get in touch
Don't miss any updates of our product.
© Workik Inc. 2026 All rights reserved.

