Join our community to see how developers are using Workik AI everyday.
Features

Build Intrusion Detection Models
AI crafts tailored IDS models leveraging datasets like KDDCup or NSL-KDD to simplify anomaly detection.

Simplify Log Analysis
AI helps parse and analyze logs using ElasticSearch, providing actionable insights to detect unauthorized activities.

Instant Threat Responses
AI enables rapid scripting of automated responses for detected threats with Python and Bash.

Optimize Security Workflows
AI assists with complex IDS configurations, ensuring seamless compatibility with Suricata and Zeek.
How it works
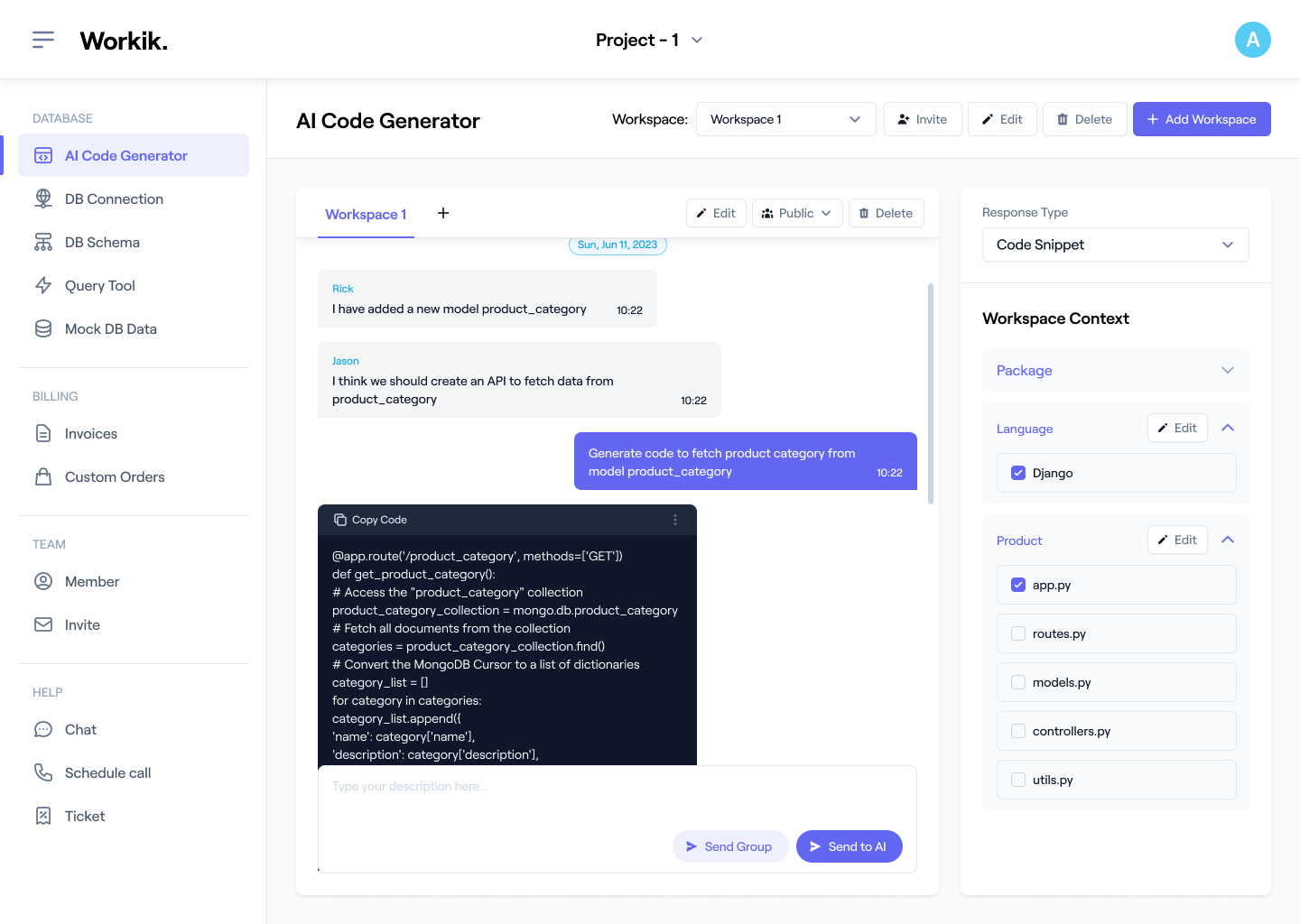
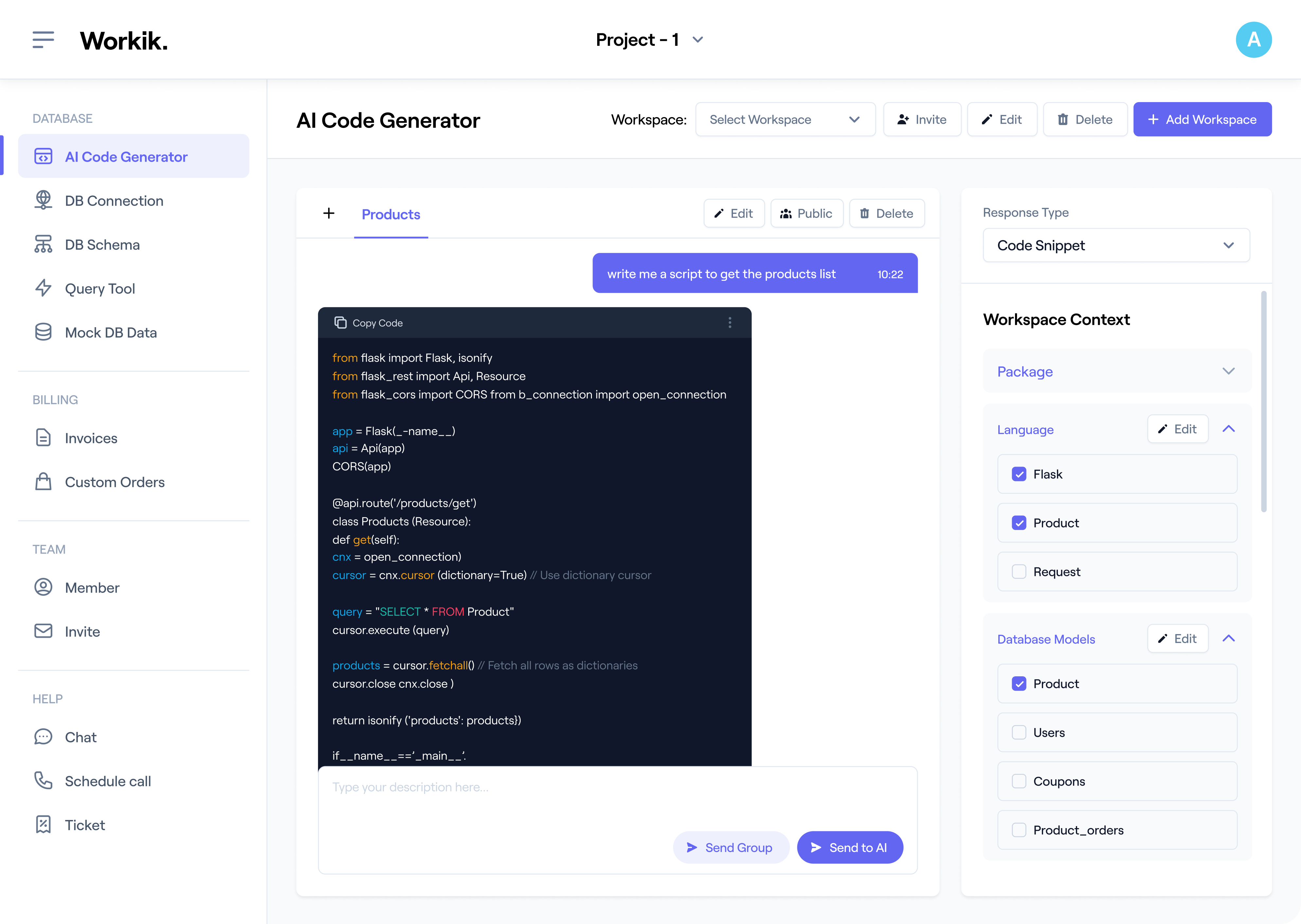
Sign up for a Workik account manually or use Google to get started on crafting your IDS code effortlessly with AI.
Import your IDS project from GitHub, GitLab, or Bitbucket. Define traffic patterns, detection rules, and alert thresholds. Specify advanced features like threat scoring, API integrations, and log analysis to optimize AI assistance.
Use AI to generate, debug & test code, analyze datasets, refine anomaly detection models, and optimize system rules. Improve system responsiveness with faster threat analysis, updates for evolving threats and more.
Invite your team to collaborate in real-time within your workspace, customizing detection strategies and sharing insights instantly. Use AI for deployment, updates, and intrusion prevention mechanisms.

Expand
.png)
.png)
Expand

Expand


Expand


Expand


Expand


Expand


TESTIMONIALS
Real Stories, Real Results with Workik
Workik AI streamlined our IDS setup and optimized threat response instantly.

Sarah Stanson
Senior Security Engineer
As a beginner, I was amazed at how AI guided me through building a robust IDS with seamless tool integration.

Kunal Patel
Junior Network Analyst
Workik AI handled IDS deployment seamlessly, from traffic analysis to model fine-tuning.

Judith Carter
DevOps Specialist
What are some popular use cases for Workik's AI-powered IDS code generator?


Workik’s AI-powered IDS code generator is ideal for a variety of use cases which include but are not limited to:
* Generate optimized detection rules for Suricata or Snort.
* Build custom machine learning models for anomaly detection.
* Automate log parsing and analysis with ElasticSearch integrations.
* Create alerting mechanisms with real-time notification systems.
* Handle network traffic simulation using Scapy or Tcpreplay.
* Configure adaptive thresholds for dynamic intrusion detection.
* Integrate behavioral analysis for zero-day attack detection.
What context-setting options are available in Workik’s AI for IDS code generator?


Workik provides various context-setting options to tailor AI-generated IDS code, where users can:
* Add detection frameworks like Suricata or Bro (Zeek).
* Import network traffic datasets for training ML-based IDS models.
* Define API endpoints for alerting and logging systems.
* Integrate GitHub, GitLab, or Bitbucket for existing IDS configurations.
* Set up behavioral models with anomaly detection frameworks.
* Include advanced logging structures for detailed forensics and analysis.
How can Workik AI-powered IDS generator help with threat correlation?


Workik AI can analyze network logs, application logs, and endpoint data, to detect complex attack patterns. For instance, it can identify patterns in DDoS attacks by combining anomalous traffic behavior and unusual server response times across various systems.
Can the AI generator create IDS setups for hybrid cloud environments?


Yes, Workik AI helps integrate public cloud logs (e.g., AWS CloudTrail) with on-premise traffic monitoring. This enables seamless detection of lateral movement between cloud services and on-premise networks.
How does Workik AI improve incident response readiness?


AI can preconfigure playbooks for IDS-triggered responses. For example, it can script automated actions like isolating infected devices, generating detailed reports for security teams, or sending alerts to SIEM tools such as Splunk.
Can Workik AI IDS generator assist in compliance reporting?


Absolutely. Workik AI generates IDS configurations that align with compliance frameworks like GDPR or PCI-DSS. It can also create audit logs and reports, ensuring your intrusion detection measures meet regulatory standards without manual intervention.
How does Workik AI handle advanced threat detection like insider attacks?


Workik AI can generate behavioral profiles of users or systems, enabling the detection of unusual patterns that may indicate insider threats. For example, it can flag anomalous file access attempts during off-hours or unusual privilege escalations.
Generate Code For Free

Intrusion Detection System (IDS): Question And Answer
An Intrusion Detection System (IDS) is a cybersecurity solution designed to monitor and analyze network traffic or system activities for malicious actions or policy violations. IDS identifies potential threats like unauthorized access, malware, or unusual traffic patterns, providing alerts to help mitigate risks. It’s a critical tool for maintaining network integrity and security.
Popular frameworks and libraries used in IDS development include:
Rule-Based Detection:
Snort, Suricata
Behavioral Analysis:
TensorFlow, PyTorch
Log Analysis:
ElasticSearch, Kibana
Network Monitoring:
Zeek (formerly Bro), Tcpreplay
Protocol Analysis:
Scapy, Wireshark
Alerting Systems:
Splunk, Nagios
Testing and Simulation:
Metasploit, Nessus
Popular use cases of IDS include:
Healthcare:
Protect patient data by detecting unauthorized access to electronic health records and complying with HIPAA.
Finance:
Monitor transactions for anomalies, prevent fraud, and secure sensitive customer data in compliance with PCI-DSS.
E-commerce:
Detect and prevent bot traffic, account takeovers, and suspicious activities during checkout processes.
Government:
Secure sensitive communication channels and monitor for espionage or sabotage attempts.
Education:
Safeguard student and staff information against cyberattacks targeting institutional databases.
Cloud Services:
Identify lateral movements or policy violations between multi-cloud environments.
Career opportunities and technical roles available for professionals in IDS include Cybersecurity Analyst, Network Security Engineer, SOC Analyst, Threat Intelligence Specialist, IDS/IPS Architect, Security Automation Engineer, Incident Response Specialist, and Penetration Tester.
Workik AI provides comprehensive IDS development assistance, which includes:
Rule Generation:
Create optimized detection rules for tools like Suricata or Snort.
Anomaly Detection Models:
Build and train machine learning models to identify unusual patterns in network behavior.
Traffic Simulation:
Simulate realistic network scenarios using tools like Scapy or Tcpreplay for IDS testing.
Log Management:
Parse, correlate, and analyze logs with ElasticSearch and Kibana to enhance threat detection.
Integration Support:
Set up seamless integration with SIEM tools for centralized threat monitoring.
Real-Time Alerting:
Configure APIs for instant alerts to Slack, Discord, or email.
Testing Environments:
Create isolated environments to test configurations against simulated threats.
Debugging Assistance:
Use AI to pinpoint issues in detection rules, optimize configurations, and troubleshoot system alerts.
Optimization:
Optimize IDS performance by automating threshold adjustments and reducing false positives.
Explore more on Workik
Get in touch
Don't miss any updates of our product.
© Workik Inc. 2026 All rights reserved.

