Join our community to see how developers are using Workik AI everyday.
Features

Generate Secure Algorithms
AI creates robust AES and RSA algorithms with OpenSSL and Bouncy Castle, ensuring industry-standard encryption.

Encrypt API & Database Data
AI applies PyCryptodome and Libsodium encryption for seamless data security and integrity across APIs and databases.

Automate Key Management
Use AI to automate key rotation and storage with AWS KMS & HashiCorp Vault, eliminating hard-coded keys.

Ensure Compliance-Ready Encryption
AI enforces FIPS 140-2 and GDPR standards, generating code that meets strict data protection requirements.
How it works
Create a free Workik account to access AI-driven encryption tools and start generating secure code instantly.
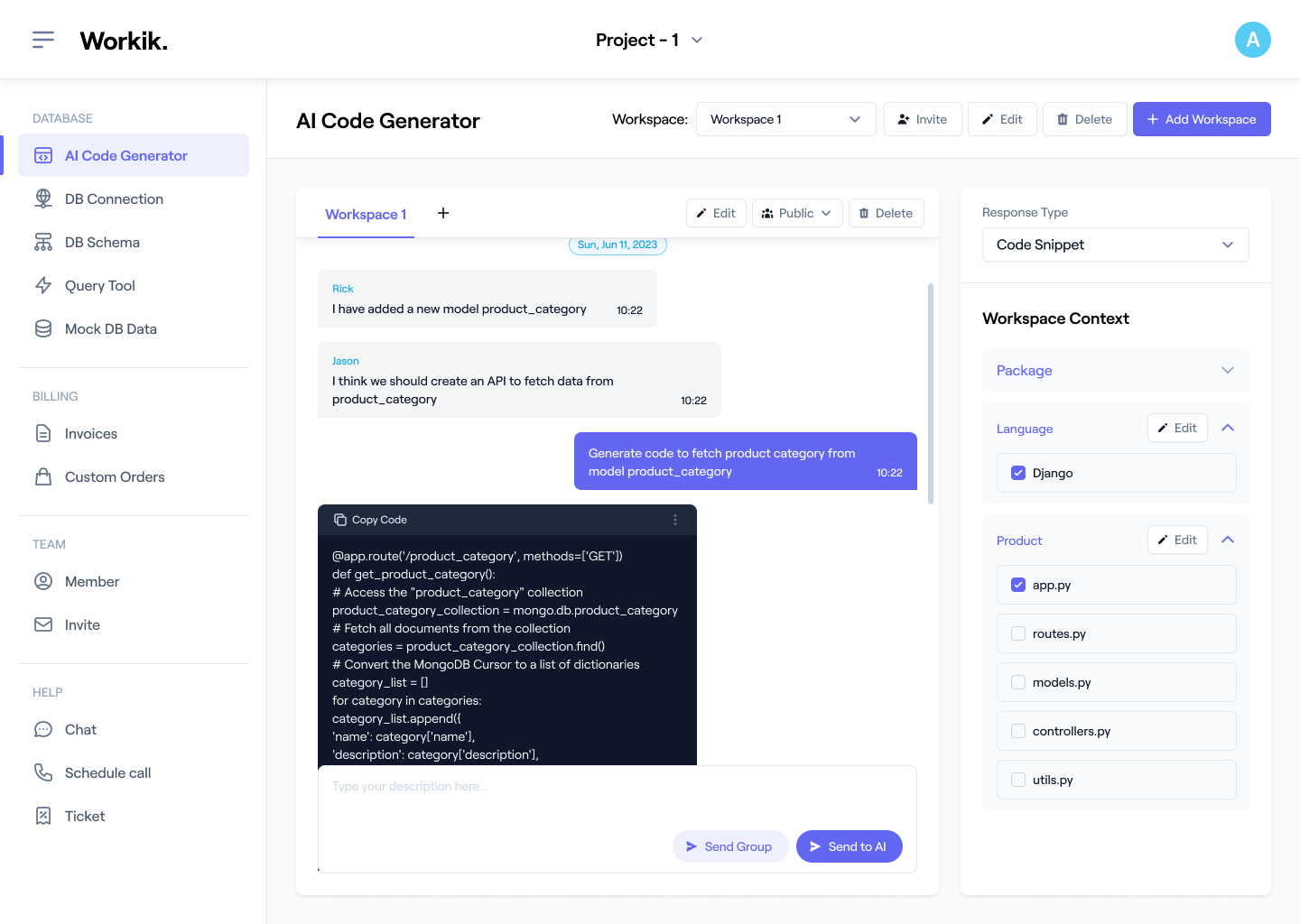
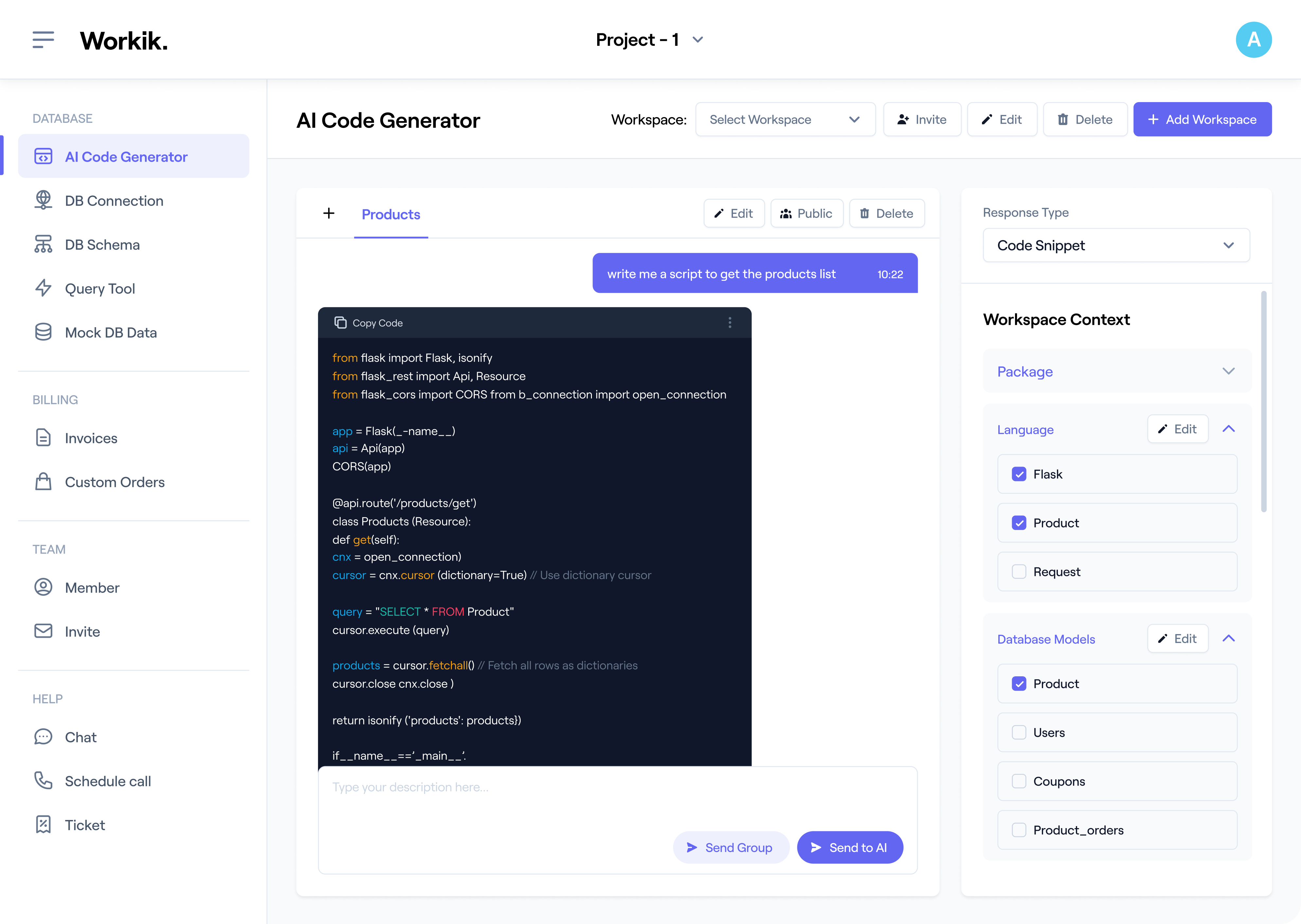
Link your GitHub, GitLab, or Bitbucket repositories. Specify encryption libraries like OpenSSL or PyCryptodome, standards such as AES or RSA, and compliance needs like GDPR for precise AI assistance.
Input encryption parameters to generate algorithms and debug issues like padding errors or key mismatches. AI also refines code for secure implementation in databases, APIs, or file systems.
Invite your team to review and refine encryption code. Test encryption workflows, ensure data security, and validate compliance effortlessly with Workik’s integrated tools.

Expand
.png)
.png)
Expand

Expand


Expand


Expand


Expand


Expand


TESTIMONIALS
Real Stories, Real Results with Workik
Workik made AES encryption for our API fast and reliable, handling code generation and debugging with ease.

Matt Anderws
Senior Backend Developer
As a junior developer, Workik’s step-by-step guidance made secure encryption simple and clear!

Karan Patel
Junior Software Developer
Workik delivered flawless end-to-end encryption for our messaging app, ready to deploy in no time.

Dominic Martinez
Full Stack Developer
What are some popular use cases of Workik’s AI for Encryption Code Generator?


Some popular use cases of Workik's AI-powered Encryption Code Generator for developers include but are not limited to:
* Generating secure AES, RSA, and SHA algorithms for APIs and databases.
* Encrypting data at rest and in transit to secure workflows.
* Enabling end-to-end encryption for messaging applications.
* Automating key generation, rotation, and management.
* Securing data to meet compliance standards like GDPR and HIPAA.
* Creating encrypted backups to prevent unauthorized access.
What are the context-setting options for Workik AI for Encryption Code Generator?


Workik offers diverse context-setting options for encryption code assistance by allowing users to:
* Linking GitHub, GitLab, or Bitbucket for importing encryption requirements.
* Defining standards like AES-256 or RSA-2048 for precise implementation.
* Adding key management tools such as AWS KMS or Azure Key Vault.
* Configuring use cases like API protection, database encryption, or file security.
* Specifying compliance parameters like GDPR or PCI DSS for regulation-ready code.
What types of encryption can I generate with Workik’s AI-powered tools?


Workik supports generating AES (Advanced Encryption Standard), RSA (Rivest-Shamir-Adleman), SHA (Secure Hash Algorithm), and ECC (Elliptic Curve Cryptography). You can create algorithms tailored for APIs, database security, file encryption, or even secure communication systems like messaging apps.
Is Workik suitable for securing large-scale databases?


Yes, Workik is designed to handle complex database encryption. It can generate code to encrypt sensitive columns, apply transparent data encryption (TDE), or secure backups, ensuring your database meets compliance and performance standards.
Can Workik be used for file encryption workflows?


Workik supports generating code for encrypting files with standards like AES-256. It’s perfect for securing sensitive documents, creating encrypted archives, or automating file security in workflows like cloud storage.
How does Workik assist in debugging encryption issues?


Workik’s AI identifies and resolves common encryption problems like incorrect key usage, padding errors, or data corruption during decryption. This ensures smooth deployment of secure solutions.
Can Workik automate certificate-based encryption for APIs?


Yes, Workik can generate code for certificate-based encryption using X.509 certificates, enabling secure API communication over HTTPS or TLS. It also assists with certificate generation and validation processes.
Generate Code For Free

Encryption: Question and Answer
Encryption is a process of encoding information to prevent unauthorized access. It transforms plaintext into ciphertext using algorithms like AES, RSA, or ECC. Only authorized parties with the correct decryption keys can access the original data. Encryption is a core technology for securing communication, protecting sensitive data, and ensuring confidentiality in modern systems.
Popular languages, frameworks, and tools used for encryption include:
Languages:
Python, Java, C++, JavaScript, Go
Frameworks:
OpenSSL, PyCryptodome, Bouncy Castle, Libsodium
Key Management:
AWS KMS, Azure Key Vault, HashiCorp Vault
Protocols:
SSL/TLS, IPsec, HTTPS
Encryption Algorithms:
AES, RSA, ECC, ChaCha20
Database Integration:
Transparent Data Encryption (TDE) in PostgreSQL, MySQL, MongoDB
Popular encryption use cases include but are not limited to:
Secure Communication:
Encrypting messaging apps and emails with end-to-end encryption (e.g., Signal, WhatsApp).
Data Protection:
Encrypting sensitive data at rest and in transit for compliance and security.
Key Management:
Automating key generation and rotation for secure cryptographic systems.
API Security:
Encrypting payloads and implementing token-based authentication (e.g., JWT).
Database Encryption:
Protecting sensitive columns and encrypting backups in databases.
File Encryption:
Securing sensitive documents for secure sharing and storage.
IoT Security:
Encrypting device communication and telemetry data.
Career Roles include Security Engineer, Cryptography Engineer, DevSecOps Specialist, Cloud Security Specialist, and Compliance Officer, focusing on securing systems and meeting regulatory standards.
Workik AI simplifies encryption development by:
Code Generation:
Automates AES, RSA, ECC, and custom encryption.
Key Management:
Handles key rotation and storage with AWS KMS and Azure Key Vault.
Debugging:
Resolves issues like padding errors and invalid key lengths.
Optimization:
Recommends lightweight algorithms like ChaCha20.
Refactoring:
Improves encryption code for maintainability and security.
Compliance:
Ensures GDPR, HIPAA, and PCI DSS compliance.
API Security:
Automates payload encryption and token handling.
Documentation:
Generates detailed encryption code documentation.
File Encryption:
Secures files for storage and sharing.
Database Security:
Encrypts columns, backups, and ensures TDE compliance.
Explore more on Workik
Get in touch
Don't miss any updates of our product.
© Workik Inc. 2026 All rights reserved.

