Join our community to see how developers are using Workik AI everyday.
Features

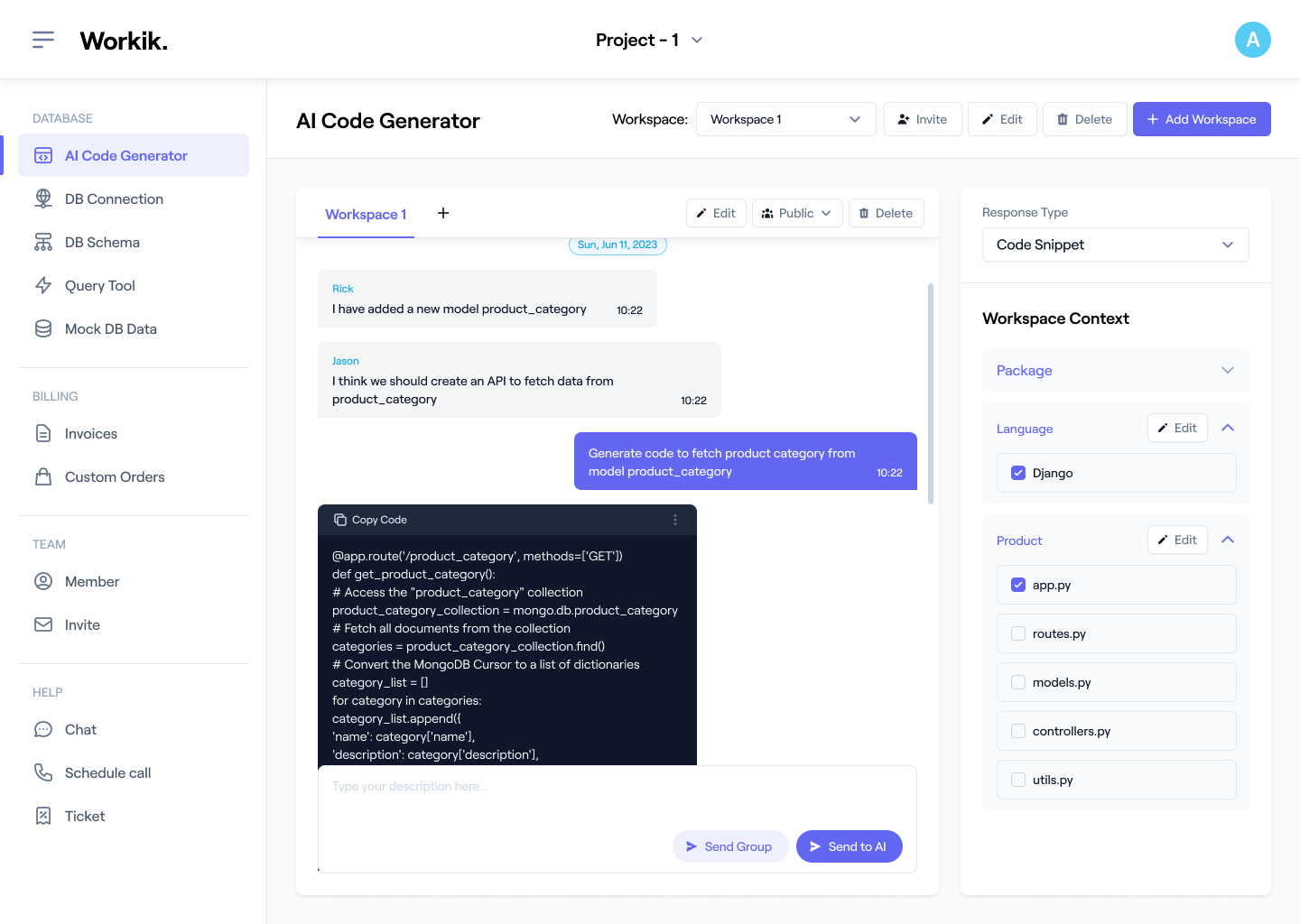
Generate CSRF Tokens
AI creates secure CSRF tokens and validates them in Django or Spring Boot, ensuring OWASP-compliant request security.

Adapt Middleware Easily
Modify middleware for AJAX in Express.js or form security in Flask, ensuring compatibility with diverse architectures.

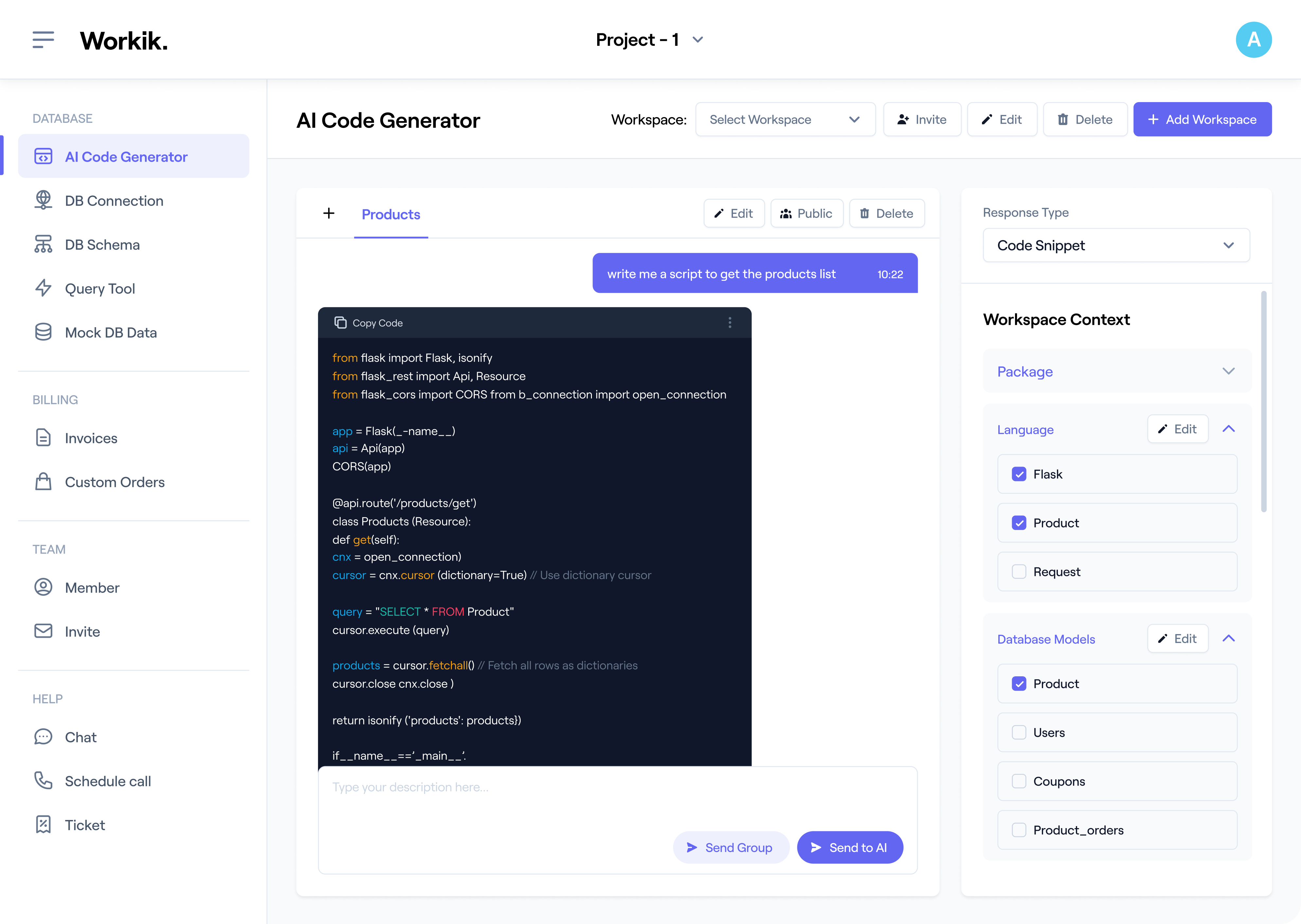
Protect APIs Effectively
Implement double-submit cookies or custom headers for robust protection in Angular or Vue.js APIs.

Validate CSRF Defenses
AI audits detect vulnerabilities and confirm token enforcement using tools like OWASP ZAP for secure endpoints.
How it works
Sign up easily using Google or manual details to access AI-driven CSRF protection tools.
Connect your GitHub, GitLab, or Bitbucket repositories. Specify frameworks like Django, Laravel, or Express.js and highlight your authentication needs for precise AI support.
Leverage AI to debug CSRF setups, optimize token validation logic, refine middleware configurations, and enhance compatibility with AJAX requests or API security workflows.
Collaborate with your team to refine implementation in shared workspaces. Use tools like OWASP ZAP to test vulnerabilities, ensuring tokens are validated correctly across all endpoints.

Expand
.png)
.png)
Expand

Expand


Expand


Expand


Expand


Expand


TESTIMONIALS
Real Stories, Real Results with Workik
Workik’s CSRF generator streamlined securing our APIs, making debugging and validation effortless.

Anthony James
Senior Backend Engineer
Integrating CSRF tokens into React and Express was fast and error-free, saving hours of work.

Rayson Claude
Full-Stack Developer
Custom headers for Angular APIs were flawless, simplifying security across endpoints.

Mitchell Shawn
Frontend Engineer
What are some popular use cases of Workik's AI-powered CSRF Protection Code Generator?


Workik’s AI-powered CSRF Protection Code Generator is ideal for a wide range of use cases which include but are not limited to:
* Protecting API endpoints with secure custom headers.
* Automating token generation and validation in Django, Laravel, and Spring Boot.
* Securing AJAX workflows in React, Angular, and Vue.js applications.
* Implementing double-submit cookies for enhanced API security.
* Strengthening session-based authentication in Express.js and Flask.
* Simplifying CSRF protection for multi-step forms and conditional workflows.
What context-setting options are available in Workik’s AI for CSRF Protection Code Generator?


Workik offers diverse context-setting options for CSRF code assistance by allowing users to:
* Connect GitHub, GitLab, or Bitbucket repositories for seamless integration.
* Choose frameworks like Node.js, Flask, Laravel, or Django for tailored CSRF setups.
* Configure session management strategies, token expiration, and rotation policies.
* Set up API workflows with custom headers and double-submit cookie options.
* Add middleware configurations for AJAX requests or form-based workflows.
* Enable cross-platform compatibility for SPAs, APIs, and mobile integrations.
Can Workik secure dynamic forms created at runtime?


Yes, Workik supports runtime form generation by automating CSRF token injection into dynamically created forms. This ensures that even forms not predefined in the codebase are protected against forgery attacks.
Does Workik provide audit trails for CSRF token usage?


Workik tracks all token-related activities, creating detailed logs of token generation, validation, and failures. This audit trail aids in debugging, compliance audits, and understanding token behavior in complex workflows.
How does Workik secure cross-origin requests in CSRF workflows?


Workik generates secure configurations for CORS policies, ensuring that tokens are validated for requests originating from trusted cross-origin domains while blocking unauthorized ones.
Can Workik create lightweight CSRF workflows for temporary apps?


Yes, Workik generates minimal yet secure token mechanisms for short-lived apps like demo portals, hackathons, or temporary environments. Tokens are tailored for quick setup and seamless teardown.
How does Workik mitigate token replay attacks?


Workik supports advanced strategies like one-time-use tokens and expiration timers, ensuring that stolen or reused tokens are invalidated immediately after a single request.
Can Workik secure asynchronous or partial form submissions?


Yes, Workik handles token validation for asynchronous or multi-part forms by creating step-specific tokens that validate each form stage without disrupting the workflow.
How does Workik address CSRF protection in PWAs (Progressive Web Applications)?


Workik generates token configurations optimized for PWAs, ensuring compatibility with offline mode, caching strategies, and service workers while maintaining robust validation.
Generate Code For Free

CSRF Protection: Question and Answer
Cross-Site Request Forgery (CSRF) protection prevents unauthorized actions on a web application by validating that requests originate from a trusted user. This is typically achieved using cryptographically secure tokens embedded in forms or headers, ensuring malicious third-party sites cannot forge requests. CSRF protection is a cornerstone of web security, safeguarding against unauthorized data modifications or sensitive operations.
Popular tools for implementing CSRF protection include:
Languages:
Python, Java, JavaScript, PHP, Ruby
Frameworks:
Django, Flask, Spring Boot, Express.js, Ruby on Rails, Laravel
Libraries:
OWASP CSRFGuard, csrf-token (npm), Django CSRF Middleware
Security Tools:
OWASP ZAP, Burp Suite
Testing Tools:
Postman, Selenium
DevOps Integrations:
Jenkins, GitHub Actions
CSRF protection is widely used in scenarios which include but are not limited to:
API Security:
Validate tokens in RESTful and GraphQL headers to block unauthorized API calls.
AJAX Requests:
Secure asynchronous workflows in React, Angular, and Vue.js with token validation.
Form Submissions:
Protect e-commerce checkouts, registrations, and multi-step forms.
Admin Actions:
Safeguard sensitive tasks like role changes and database updates.
Third-Party Integrations:
Ensure secure token validation for external service requests.
SPAs:
Automate CSRF token handling for dynamic content in Single Page Applications.
Mobile Backends:
Secure API calls from mobile apps with session-based or token-based CSRF checks.
Microservices:
Embed CSRF validation in service middleware for secure inter-service communication.
CSRF protection offers roles like Web Application Security Engineer, Backend Developer, DevOps Engineer, Penetration Tester, and API Security Specialist, with work ranging from implementing middleware and validating tokens to designing secure APIs and automating CSRF checks in CI/CD pipelines.
Workik AI simplifies CSRF implementation with:
Token Generation:
Creates secure tokens for forms, APIs, and AJAX workflows.
Middleware Automation:
Configures CSRF middleware for popular frameworks.
Debugging and Optimization:
Detects misconfigurations and refines token validation logic.
Custom Headers:
Automates secure headers for API protection.
Security Audits:
Validates defenses with tools like OWASP ZAP.
Documentation:
Generates comprehensive guides for CSRF workflows.
Cross-Platform Support:
Secures SPAs, mobile apps, and serverless setups.
Explore more on Workik
Get in touch
Don't miss any updates of our product.
© Workik Inc. 2026 All rights reserved.

