Join our community to see how developers are using Workik AI everyday.
Features

Generate Custom Mitigation Rules
AI uses iptables and AWS WAF best practices to create precise, traffic-sensitive rules that minimize disruptions.

Automate Attack Detection
Leverage AI to seamlessly integrate Scikit-learn or TensorFlow to detect traffic anomalies and trigger responses instantly.

Deploy API-Driven Defense
AI configures Cloudflare Workers and AWS Lambda for automated, API-compatible workflows.

Enhance Load Optimization
AI employs Apache JMeter to simulate attacks, identify bottlenecks and optimize network configurations.
How it works
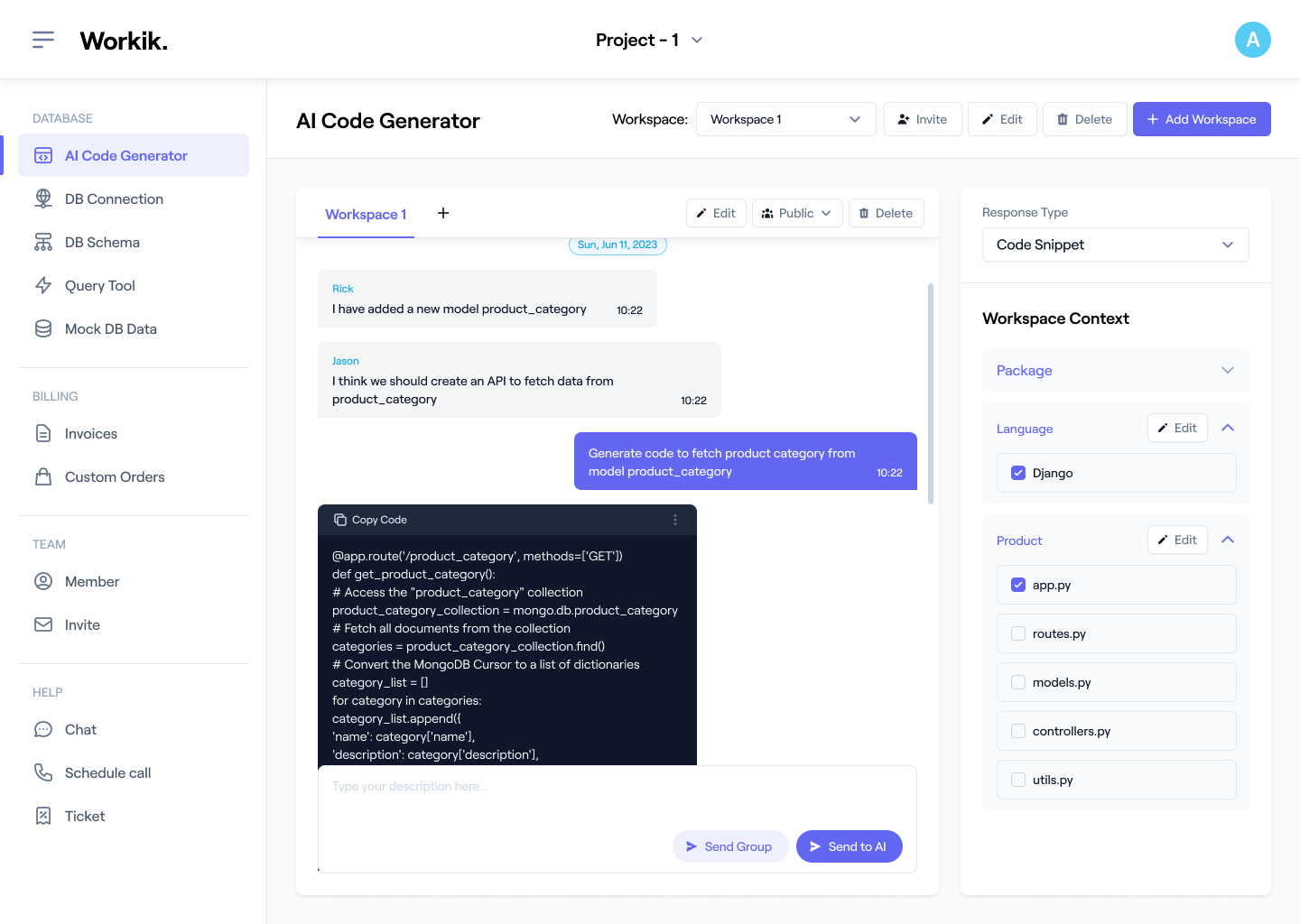
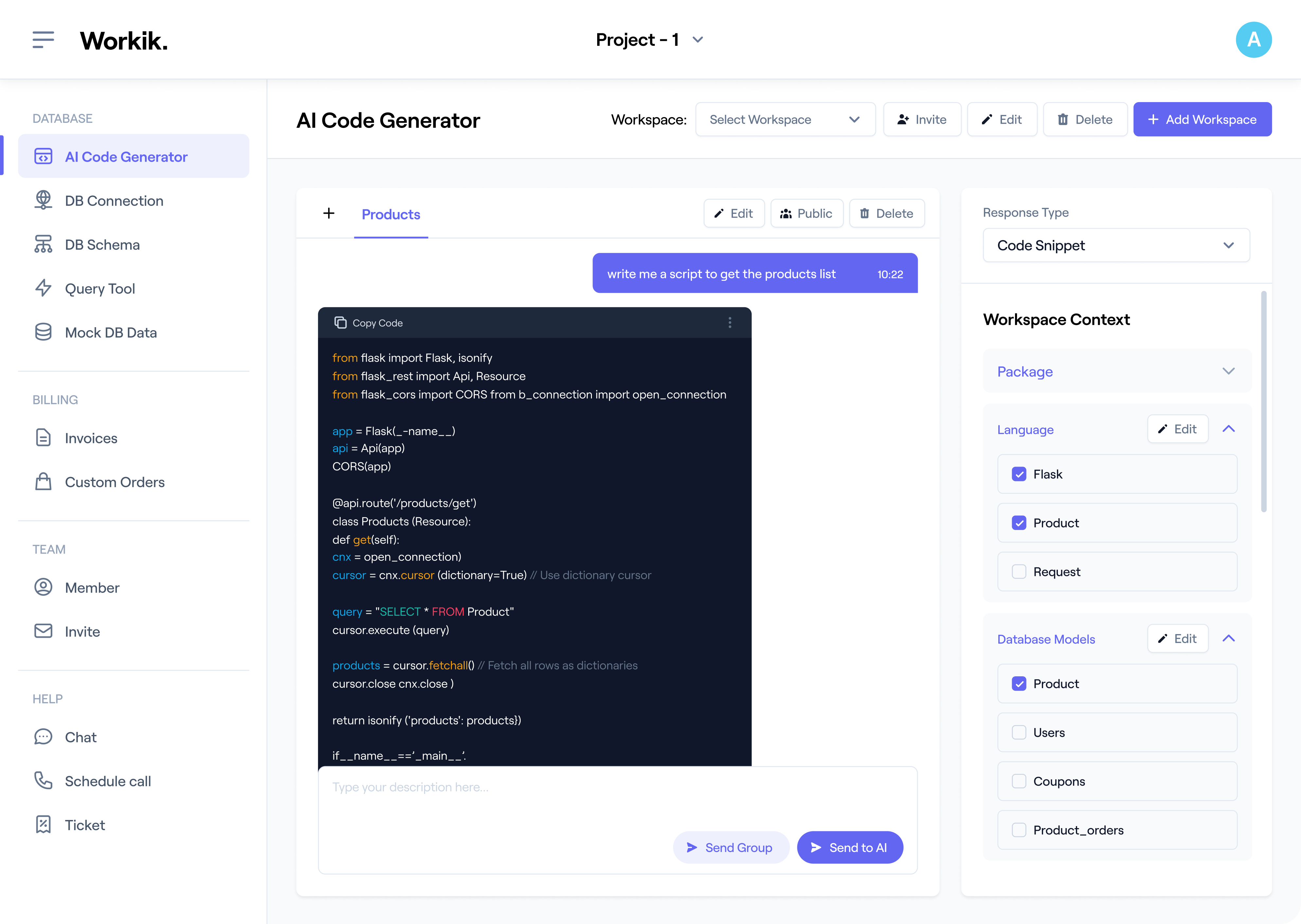
Create your Workik account manually or sign in with Google, and start crafting DDoS mitigation code with AI.
Import network configurations from GitHub, GitLab, or Bitbucket. Define firewall rules, traffic patterns, and thresholds. Specify additional needs like API integrations or load balancing to tailor AI responses.
Leverage AI to create dynamic traffic filters, generate detection algorithms, automate response workflows, or optimize network defenses. AI adapts to your project context, ensuring precise and effective DDoS mitigation.
Invite your team to the workspace for real-time collaboration. Continuously refine your DDoS strategy by testing new scenarios, fine-tuning rules, and integrating advanced defensive measures.

Expand
.png)
.png)
Expand

Expand


Expand


Expand


Expand


Expand


TESTIMONIALS
Real Stories, Real Results with Workik
Workik AI automated DDoS rule creation has transformed how I monitor and secure traffic—efficient and precise!

Emily Carter
Network Administrator
Workik AI streamlined API-based DDoS defenses, cutting integration time and enhancing response reliability.

Rajesh Kumar
Software Developer
Workik’s anomaly detection and AI attack simulations are invaluable for crafting advanced mitigation strategies.

Chloe Anderson
Cybersecurity Consultant
What are some popular use cases of Workik's AI-powered DDoS Mitigation Code Generator?


Some popular use cases of the DDoS Mitigation Code Generator include but are not limited to:
* Automate firewall rule creation for detecting and blocking malicious traffic.
* Develop traffic anomaly detection systems for early threat identification.
* Build custom rate-limiting mechanisms to prevent resource exhaustion.
* Implement adaptive filtering systems for dynamically evolving attack patterns.
* Automate API-driven DDoS response workflows for seamless mitigation.
* Simulate DDoS attack scenarios to test and optimize network resilience.
What context-setting options are available in Workik’s AI for DDoS Mitigation Code Generator?


Workik offers diverse context-setting options for DDoS mitigation code assistance, allowing users to:
* Specify iptables or AWS WAF rulesets for precise traffic control.
* Add known traffic patterns or threat signatures for customized rule generation.
* Import network configurations or monitoring scripts from GitHub, GitLab, or Bitbucket.
* Define thresholds and actions for rate-limiting and resource protection.
* Set API integration parameters for managing mitigation workflows.
How does Workik AI simplify the creation of dynamic traffic filters?


Workik AI analyzing patterns from real-world DDoS logs. For instance, it can create iptables rules to block specific IP ranges, prioritize legitimate traffic, or detect repetitive attack vectors like SYN floods. This enables network administrators to prevent threats without disrupting user experience.
Can I use Workik AI to integrate DDoS mitigation into CI/CD pipelines?


Absolutely! Workik AI enables seamless integration with Jenkins and GitHub Actions. You can automate deployment of updated traffic filters or anomaly detection models. For example, as new attack patterns are identified, AI can help roll out updated mitigation scripts to production.
How does Workik AI handle multi-layered DDoS attacks?


Workik’s AI can generate mitigation strategies tailored for multi-vector attacks, such as volumetric, application-layer, and protocol-based DDoS. It can suggest load balancer configurations for high traffic volumes while simultaneously recommending rules to block slow HTTP attacks.
Can Workik AI help with geo-based DDoS mitigation strategies?


Yes, Workik AI can generate geo-restriction rules based on regional traffic analysis. For example, it can suggest blocking or rate-limiting traffic from specific countries during suspicious activity spikes while allowing legitimate users from other regions uninterrupted access.
How does Workik AI handle botnet-specific DDoS attacks?


Workik AI analyzes user-agent strings, request headers, and behavioral patterns. For instance, it can deploy honeypots to identify malicious bots and add them to a blocklist, strengthening your defenses against botnet-driven traffic floods.
Generate Code For Free

DDoS Mitigation: Question and Answer
DDoS Mitigation refers to the methods and technologies used to detect, prevent, and respond to Distributed Denial of Service (DDoS) attacks. These attacks overwhelm systems with illegitimate traffic, causing disruption to services. Effective mitigation strategies analyze traffic patterns, identify malicious requests, and deploy real-time defenses to maintain normal operations.
Popular frameworks and libraries used in DDoS mitigation include:
Firewalls and Traffic Filters:
iptables, AWS WAF
Traffic Analysis Tools:
Wireshark, Zeek
Load Balancers:
NGINX, HAProxy
Anomaly Detection Frameworks:
TensorFlow, Scikit-learn
Testing Tools:
LOIC, Apache JMeter
Cloud Platforms:
Cloudflare, Azure DDoS Protection
Popular use cases of DDoS mitigation include:
Network Protection:
Block malicious traffic while ensuring legitimate user access during an attack.
API Safeguarding:
Prevent disruption in API endpoints by deploying rate limiting and anomaly detection.
Web Application Security:
Protect web applications from volumetric and application-layer DDoS attacks.
Cloud Infrastructure Defense:
Manage and protect multi-cloud environments from targeted disruptions.
Data Center Hardening:
Safeguard data centers with scalable, automated mitigation strategies.
Career opportunities and technical roles available in DDoS mitigation include Cybersecurity Analyst, Network Security Engineer, Cloud Security Specialist, Traffic Optimization Specialist, Incident Response Analyst, DDoS Solution Architect, and Application Security Engineer.
Workik AI provides comprehensive support for DDoS mitigation development, including:
Code Generation:
Automate the creation of firewall rules, rate-limiting scripts, and anomaly detection algorithms.
Traffic Analysis:
Generate scripts for real-time traffic monitoring and anomaly identification.
Response Automation:
Create workflows to deploy countermeasures, such as IP blocking or request throttling.
Testing and Simulation:
Simulate DDoS attacks using tools like Apache JMeter and optimize defenses accordingly.
Integration Assistance:
Help integrate API-based DDoS defenses with third-party services like Cloudflare, Azure, or Google Cloud Armor.
Collaborative Features:
Enable team-based project management for deploying and maintaining DDoS mitigation solutions.
Explore more on Workik
Get in touch
Don't miss any updates of our product.
© Workik Inc. 2026 All rights reserved.

