Join our community to see how developers are using Workik AI everyday.
Supported AI models on Workik
GPT 5.2 Codex, GPT 5.2, GPT 5.1 Codex, GPT 5.1, GPT 5 Mini, GPT 5
Gemini 3.1 Pro, Gemini 3 Flash, Gemini 3 Pro, Gemini 2.5 Pro
Claude 4.6 sonnet, Claude 4.5 Sonnet, Claude 4.5 Haiku, Claude 4 Sonnet
Deepseek Reasoner, Deepseek Chat, Deepseek R1(High)
Grok 4.1 Fast, Grok 4, Grok Code Fast 1
Models availability might vary based on your plan on Workik
Features

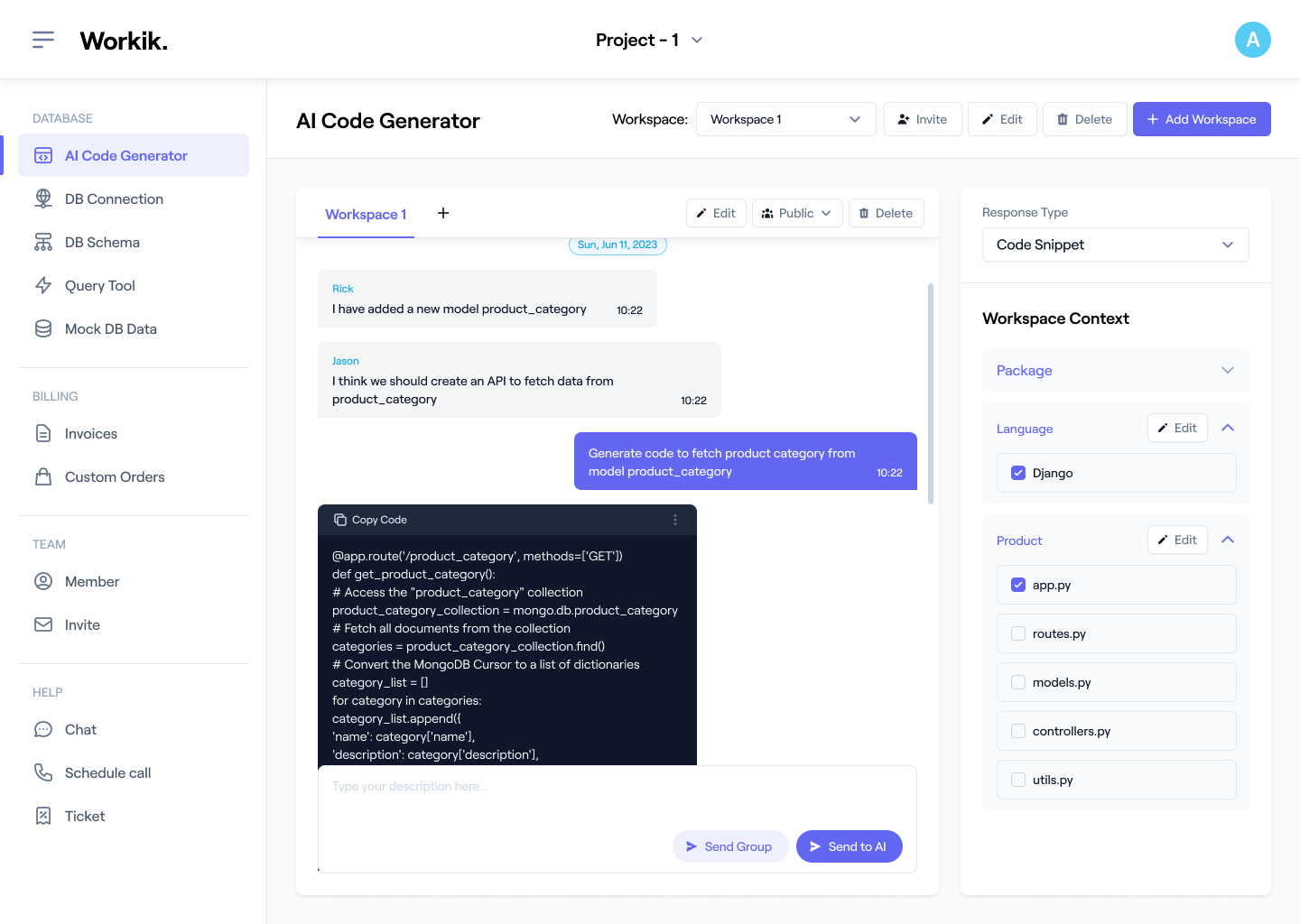
Scan Entire Codebase
Analyze complete repositories, monorepos, & microservices to detect security flaws across files or modules.

Audit Legacy Codebases
Detect and Apply fixes suggested by AI for outdated crypto, unsafe patterns, and injection risks in legacy codebases.

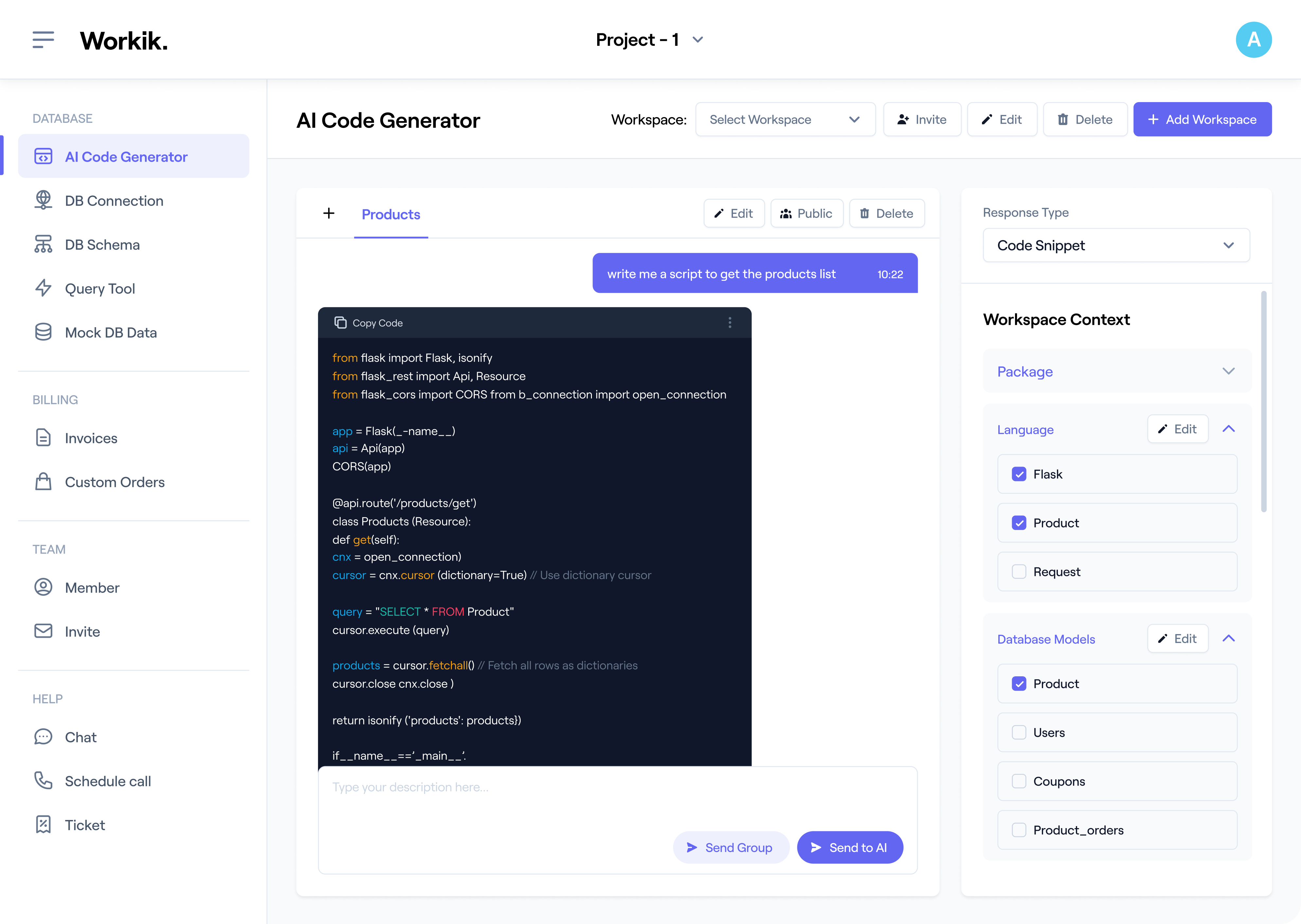
Secure CI Builds
Automatically block builds in CI/CD when critical vulnerabilities exceed defined severity thresholds

Export Detailed Scan Reports
Generate shareable HTML, JSON, or Markdown reports for security reviews, audits, or compliance checks.
How it works

Expand
.png)
.png)
Expand

Expand


Expand


Expand


Expand


Expand


TESTIMONIALS
Real Stories, Real Results with Workik
Workik AI saved me during a review. It flagged a logic flaw I completely missed in a critical route.

Rahul Deshmukh
Python Developer
Thank God I used Workik AI to check all our PRs, it caught a broken access bug right before the merge!

Meera Iyer
Application Security Analyst
Workik AI saved us big time. It scanned our legacy repo and flagged an exposed AWS key hidden deep in config.

Martin Santiago
Security Engineer
What are the most common use cases of Workik AI-Powered Code Vulnerability Scanner for developers?


Workik AI helps developers detect security risks early and ship safer code. Common use cases include but are not limited to:
- Scan login flows for missing access checks or weak session handling
- Detect hardcoded secret leaks like API keys, AWS credentials, or tokens in config files
- Block PRs with risky code patterns like eval(), exec(), or raw SQL
- Review third-party packages or open-source code for vulnerable or unsafe usage
- Scan Dockerized and serverless code for exposed env vars or insecure defaults
- Audit legacy projects for deprecated crypto, file upload flaws, or unsanitized input
- Run pre-merge scans on services inside monorepos or specific API stacks
What type of context can I set for better vulnerability scanning in Workik AI?


Adding context is important for Workik AI to detect vulnerabilities and provide tailored fix suggestions for your codebase. You can set the context by:
- Connecting GitHub, GitLab, or Bitbucket repositories
- Selecting specific folders or services to scan, like /auth or /payments
- Uploading individual files or directories manually
- Including config files like .env, docker-compose.yml, or package.json
- Scanning pull requests or commit diffs to focus on recent code changes
Can Workik AI’s Code Vulnerability Scanner detect leaked confidential data, and misconfigurations in codebases?


Yes. Workik AI scans .env, config files, and source code to detect exposed confidential data, credentials, tokens, and misconfigurations. It flags issues like hardcoded AWS keys in frontend files or Firebase tokens in backend routes and suggests secure handling using environment variables or secret managers.
Do I need to configure rulesets or write policies for the Vulnerability Scans?


Nope. Workik AI requires zero manual configuration. It understands project context, coding conventions, and best practices out of the box. However, for advanced users, you can set custom rules (e.g., reject commits exposing .env files or using weak hashing algorithms like MD5).
How does Workik AI Code Vulnerability Scanner integrate into our existing DevSecOps pipeline?


You can plug Workik AI-powered Code Vulnerability Scanner into your CI/CD workflows using GitHub Actions, GitLab CI, or Bitbucket Pipelines. Run vulnerability scans on every push, block merges when critical vulnerabilities are found, and trigger scans on open pull requests. It also goes further by providing AI-enhanced remediation paths and tighter integration with your repo context.
Can Workik AI-powered Code Vulnerability Scanner help with legacy systems or monolithic applications?


Yes. Workik AI can quickly scan large, older codebases to find security issues that manual reviews often miss. It detects things like outdated libraries, weak encryption, missing input checks, and insecure patterns, even in messy or undocumented code.
How is Workik better than linters or basic SAST tools?


While linters enforce style and some security rules, Workik AI understands code semantics, not just syntax. It tracks data flows, understands control structures, and flags issues traditional SAST tools miss—like logic flaws, implicit trust boundaries, or unsafe chaining in async workflows.
Can Workik AI’s Code Vulnerability Scanner help with scanning open-source or third-party dependencies?


Yes. Workik AI can scan external codebases before you adopt them—flagging risky functions, outdated libraries, insecure patterns, and misconfigured defaults.
Does Workik AI support scoped scanning in monorepos or modular architectures?


Absolutely. Workik AI lets you scope scans to specific folders, services, or modules which is ideal for monorepos and multi-service architectures. It helps teams run targeted scans without reprocessing the entire codebase.
Can't find answer you are looking for?
Request question

Request question
Please fill in the form below to submit your question.
Generate Code For Free

CODE VULNERABILITY SCANNING Q&A
Code vulnerability scanning is the process of analyzing source code, and codebases to identify security flaws, logic weaknesses, misconfigurations, and exposed secrets—before they reach production.
A wide range of critical vulnerabilities can be detected through code scanning, including:
- Injection flaws like SQL injection and command injection
- Cross-Site Scripting (XSS) vulnerabilities
- Insecure deserialization that may lead to remote code execution
- Hardcoded credentials, tokens, or API keys
- Weak authentication or session management practices
- Misconfigured security policies, including missing headers or lax CSPs
- Outdated or vulnerable third-party dependencies
Code vulnerability scanning helps secure your code at every stage of development. Key use cases include:
- Scanning PRs for insecure auth, unsafe eval(), or missing validation
- Detecting hardcoded secrets and tokens in config or .env files
- Auditing legacy code for weak crypto, file upload flaws, or outdated logic
- Reviewing third-party or open-source code for risky dependencies
- Blocking CI/CD deployments with high-severity security risks
Workik AI streamlines secure development workflows through intelligent analysis, fix suggestions, and automations:
Vulnerability Detection:
Identify injection flaws, broken access control, logic errors, and hardcoded secrets in code.
Context Awareness:
Tailor scans based on project language, structure, and framework for highly relevant results.
Automated Remediation:
Generate AI-powered fixes for insecure logic, unsafe patterns, or leaked credentials.
Scoped Scanning:
Run targeted scans on specific folders, services, or commit diffs without scanning entire repos.
Pipeline Integration:
Automate security checks in GitHub, GitLab, or Bitbucket to block risky deployments.
Secrets Detection:
Flag exposed tokens, credentials, and config leaks in .env, YAML, or source files instantly.
Explore more on Workik
Get in touch
Don't miss any updates of our product.
© Workik Inc. 2026 All rights reserved.

