Join our community to see how developers are using Workik AI everyday.
Features

Identify Network Risks
Detect vulnerabilities with AI-powered scans via Metasploit and OpenVAS, covering ports, protocols, and applications.

Automate Testing Workflows
Use AI to effectively simulate attacks with Burp Suite and Intruder for vulnerability, SQL injection, XSS scans, and more.

Generate Security Insights
Rank risks by severity with MITRE ATT&CK, receiving prioritized, actionable steps from Workik AI.

Boost Code Compliance
AI can give reviews aligned with OWASP, using Veracode and Checkmarx to catch security flaws early.
How it works
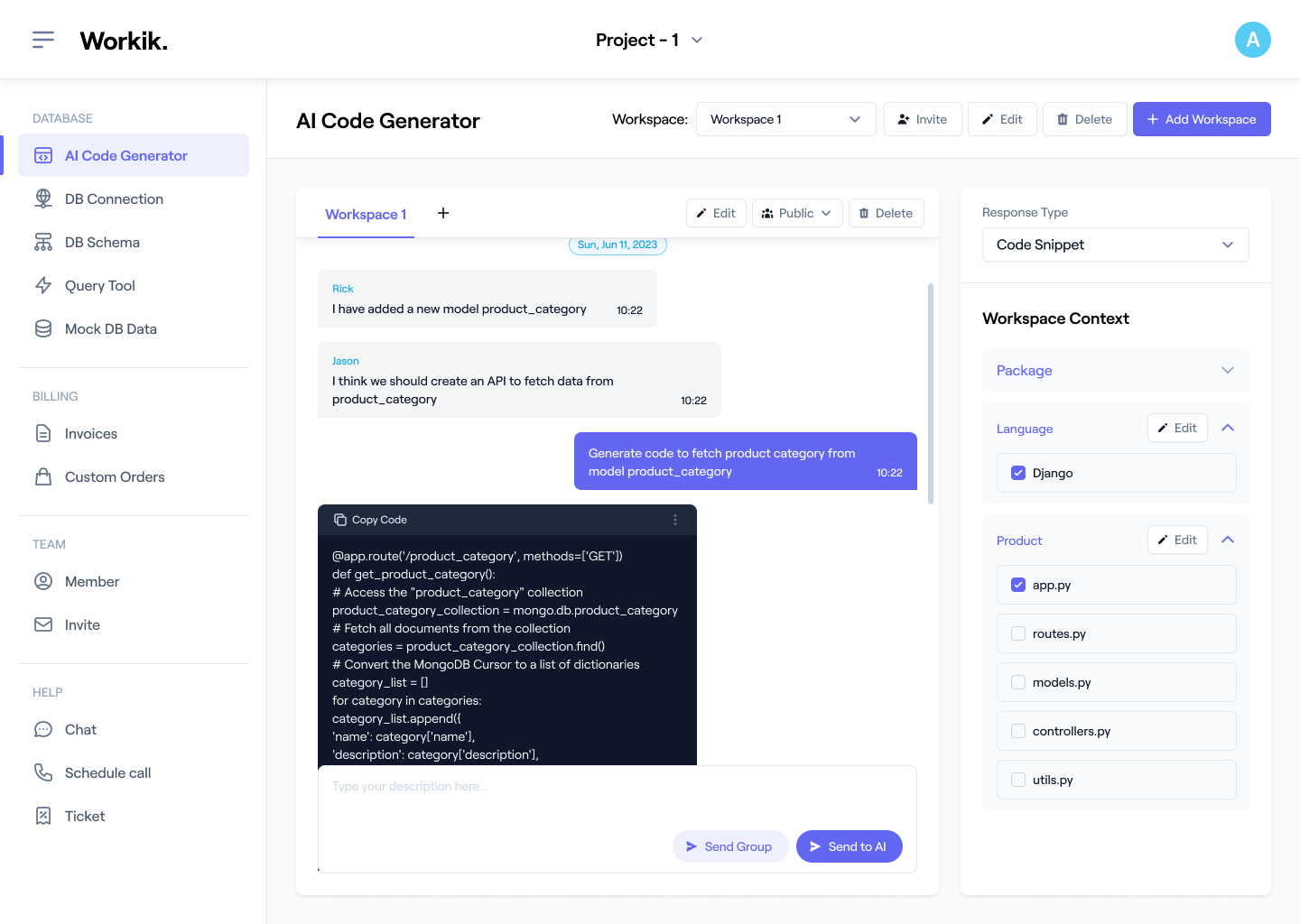
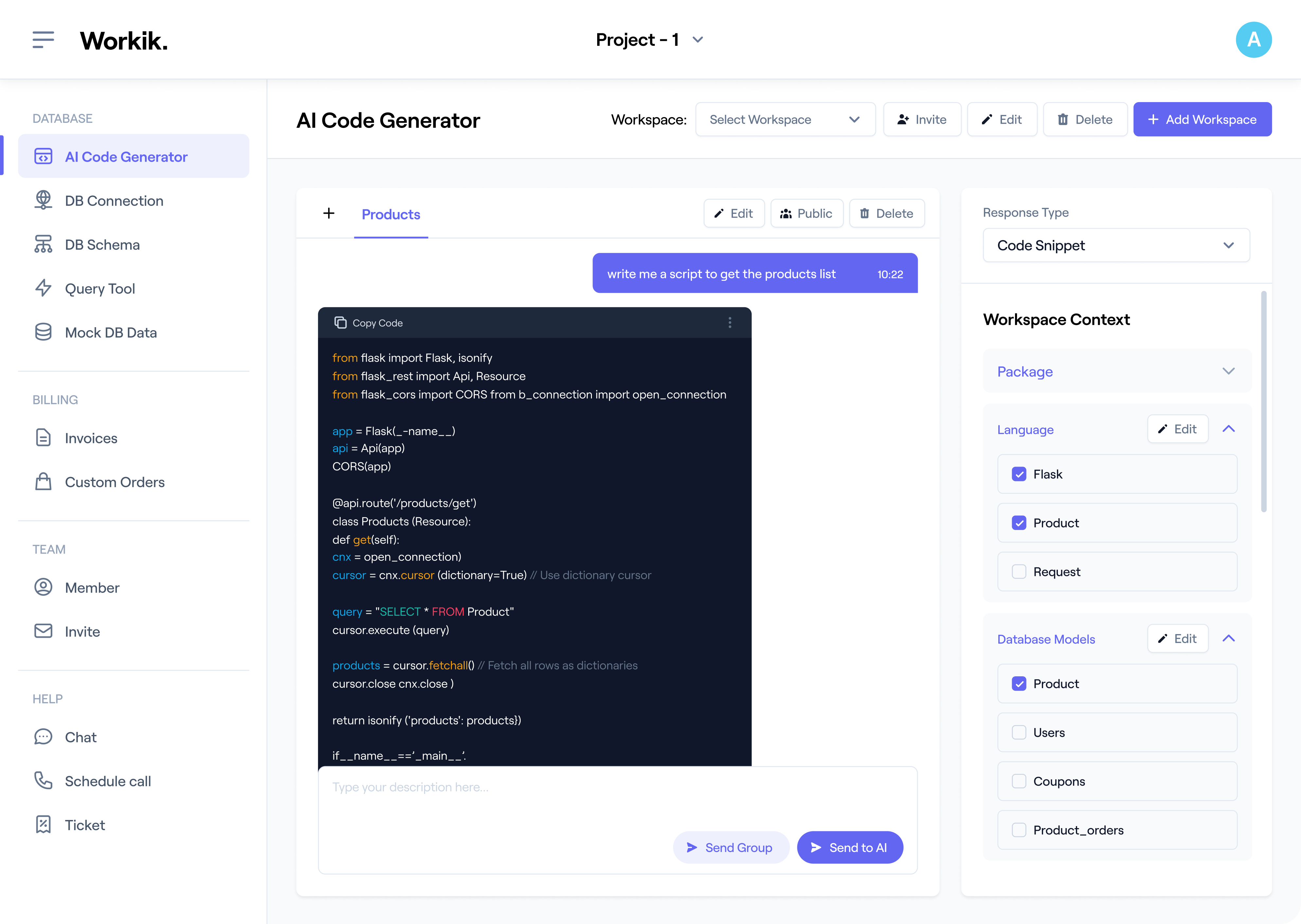
Register quickly via Google or manually to access AI-powered penetration testing tools.
Sync code repositories from GitHub, GitLab, or Bitbucket. Define testing parameters like target IPs, protocols, and network scope for tailored AI assistance.
Use AI to launch targeted penetration tests, including vulnerability scans, brute-force tests, privilege escalation attempts, and more.
Review AI-generated insights with your team in real-time, prioritize risks, and implement security fixes across your infrastructure seamlessly.

Expand
.png)
.png)
Expand

Expand


Expand


Expand


Expand


Expand


TESTIMONIALS
Real Stories, Real Results with Workik
Workik AI made penetration testing fast and precise. We identify vulnerabilities instantly and focus on fixes!

Jordan Lee
Senior DevOps Engineer
As a junior dev, I found Workik AI’s attack simulations easy and insightful—a huge boost to my security skills!

Priya Kapoor
Junior Developer
Workik AI saves us hours with accurate vulnerability insights, helping us secure applications quickly.

Michael Tanaka
Security Engineer
What are the popular use cases of Workik's AI for AI-powered penetration testing?


Popular use cases for Workik's AI in penetration testing include but are not limited to:
* Detect network vulnerabilities with automated scans and AI-driven risk assessments.
* Simulate realistic attacks like SQL injection, cross-site scripting, and brute-force tests.
* Generate compliance-focused audits aligned with OWASP, PCI DSS, and NIST standards.
* Strengthen API security by testing endpoints and validating access controls.
* Optimize firewall rules and access controls based on AI-recommended configurations.
What kind of context can I add in Workik AI related to AI-powered penetration testing?


Setting context in Workik is optional but enhances AI-generated penetration testing results. Here are the types of context you can add:
* Testing parameters (e.g., target IP ranges, protocols, ports)
* Codebase files (import security-sensitive projects from GitHub, GitLab, or Bitbucket)
* Tools and frameworks (e.g., Metasploit, Burp Suite, Nessus)
* Compliance frameworks (e.g., OWASP guidelines, NIST standards)
* API blueprints (e.g., Postman or Swagger to assess API security and monitor data flows)
How does Workik AI help prioritize vulnerabilities in large networks?


Workik AI categorizes vulnerabilities by severity, enabling teams to focus on the most critical threats first. For example, in networks with hundreds of endpoints, it uses machine learning to assess exploitability and impact, ensuring top-priority risks are addressed effectively.
Can Workik AI support penetration testing in hybrid cloud environments?


Yes, Workik AI performs across on-premises and cloud infrastructure, identifying hybrid-specific risks like misconfigured permissions and unsecured storage. It provides a unified security overview, covering both cloud and traditional assets.
How can Workik AI improve our incident response plan?


Beyond detecting vulnerabilities, Workik AI strengthens incident response by simulating breach scenarios and suggesting response steps. For instance, if a SQL injection risk is found, Workik AI offers immediate containment and remediation advice, shortening response times.
How does Workik AI assist in regulatory compliance for penetration testing?


Workik AI integrates compliance checks for standards like GDPR, HIPAA and SOC 2, aligning tests with regulatory needs. It generates detailed compliance reports with actionable steps, helping organizations meet requirements efficiently without additional tools.
How does Workik AI assist with securing privileged accounts in penetration testing?


Workik AI identifies and evaluates privileged accounts, a frequent target in attacks, by testing for misconfigurations and improper access permissions. For instance, it flags accounts with excessive privileges or weak passwords, helping teams enforce the principle of least privilege.
Generate Code For Free

Penetration Testing: Question and Answer
Penetration testing, or "pen testing," is a cybersecurity practice that simulates cyber attacks on systems or applications to identify vulnerabilities. It helps organizations discover security weaknesses, prioritize risks, and strengthen defenses before real threats can exploit them.
Popular frameworks and tools in AI-powered penetration testing include:
Vulnerability Scanning:
Nessus, OpenVAS, Acunetix
Threat Intelligence:
MITRE ATT&CK, ThreatConnect
Network Mapping:
Nmap, Shodan
Exploit Frameworks:
Metasploit, Cobalt Strike
Testing:
Selenium, Burp Suite
Network Security Audits:
Continuous audits to secure financial networks, protecting sensitive data for banks and insurance firms.
E-commerce Application Security:
Simulate attacks like SQL injection to protect customer data on e-commerce and retail platforms.
Cloud Infrastructure Protection:
Secure multi-cloud setups for tech and media companies.
Compliance Testing:
Ensure HIPAA, PCI DSS, and GDPR compliance, essential for healthcare, government, and finance sectors.
API Endpoint Security:
Protect APIs against data leaks, vital for FinTech, SaaS, and social media platforms managing sensitive data.
Career opportunities include roles such as Cybersecurity Analyst, Penetration Tester, Security Engineer, Threat Intelligence Analyst, and Incident Response Specialist. Advanced roles like AI Security Architect or Cybersecurity Data Scientist are also emerging, focusing on developing and integrating AI models into security strategies.
Vulnerability Scanning:
Automates network scans to identify and prioritize high-risk vulnerabilities.
Threat Simulation:
Generates scripts for attack simulations like brute-force, SQL injection, and XSS to test security readiness.
Compliance Analysis:
Produces audit reports aligned with standards like OWASP, NIST, and PCI DSS, helping maintain regulatory compliance.
Automated Remediation:
Suggests and assists with patching and configuration fixes based on detected vulnerabilities.
API Security Testing:
Analyzes API endpoints and generates security checks to prevent data leaks or unauthorized access.
Incident Planning:
Simulates breach scenarios, providing strategies for incident response and containment.
Performance Reports:
Delivers comprehensive reports on system security status, highlighting high-priority areas and recommended improvements.
Explore more on Workik
Get in touch
Don't miss any updates of our product.
© Workik Inc. 2026 All rights reserved.

